Total Attack Chain Coverage
Fortra’s cloud-native cybersecurity platform is designed to reduce tool sprawl by bringing complementary capabilities into a single, unified experience. The goal is simple: help organizations improve protection and operational efficiency by consolidating what they need, aligning visibility and workflows across solutions, and scaling coverage as requirements grow.
Advanced offensive and defensive security solutions covering the entire attack chain at any stage, without the overhead of managing disconnected tools
Data Protection
Fortra Data Protection focuses on helping organizations identify sensitive information, control how it’s handled, and prevent exposure across endpoints and the cloud—supporting modern collaboration without losing governance.
DSPM (Data Security Posture Management)
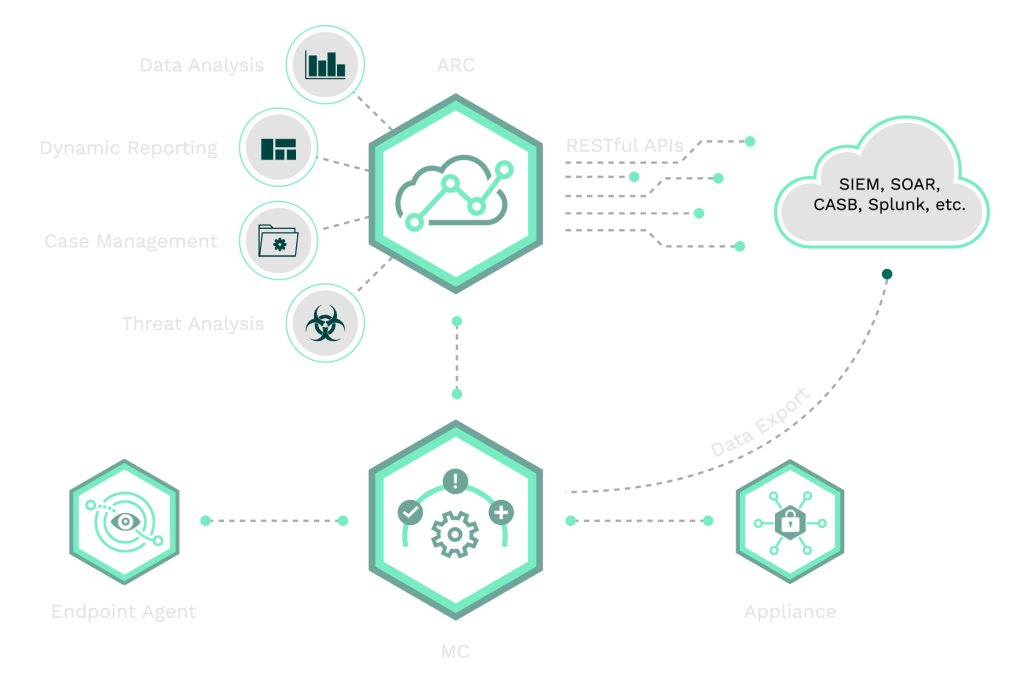
Fortra DSPM continuously discovers and maps sensitive data across on-prem, cloud, and SaaS environments to improve visibility into where data lives and how it’s being used. It emphasizes risk-based prioritization (sensitivity, exposure, business impact) to reduce noise and drive faster remediation—especially around misconfigurations, shadow data, and excessive access.
What it helps with:
- Visibility across hybrid/multi-cloud data ecosystems
- Prioritizing the highest-risk data exposures first
- Proactively identifying posture gaps before they become incidents
Cloud Data Protection
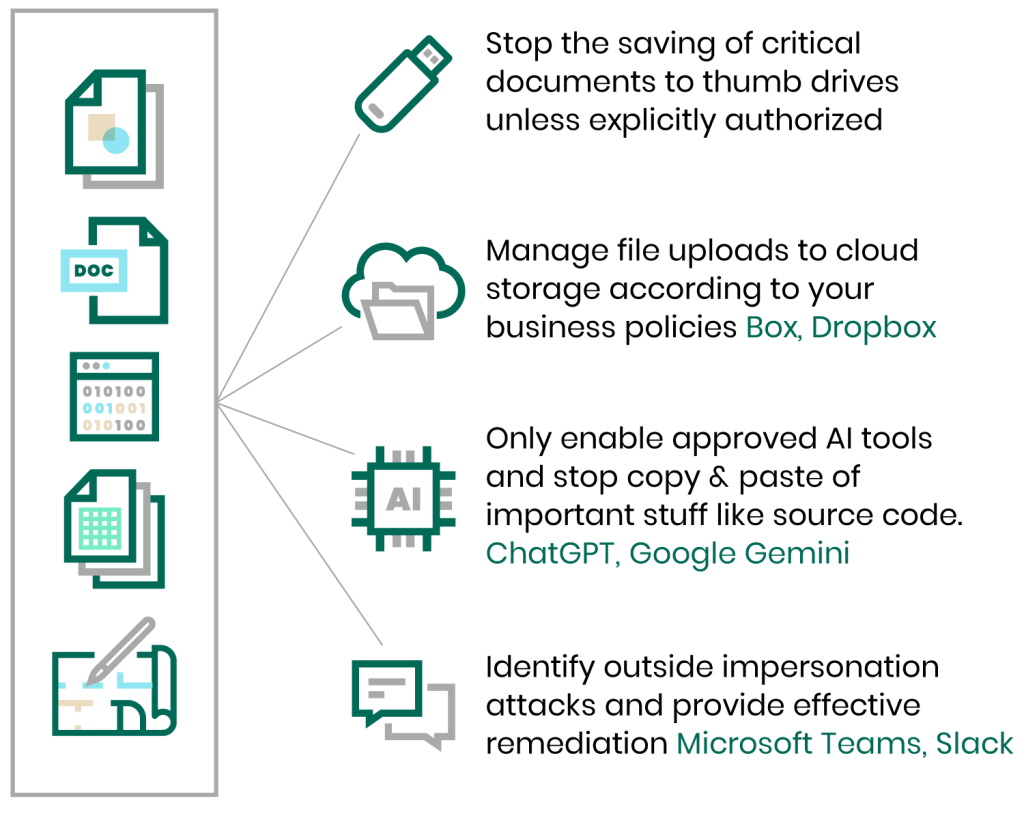
Cloud Data Protection extends DLP principles into cloud usage by combining DLP with adjacent controls to help protect sensitive data from endpoint to cloud without disrupting productivity. It’s positioned for teams that need consistent policies across cloud apps and services as data moves and is shared.
What it helps with:
- Consistent protection across cloud-stored and cloud-shared data
- Reducing risky data exposure through unified cloud controls
Data Classification
Fortra Data Classification applies visual and metadata labels to data so it stays controlled wherever it travels—supporting everything from user-driven labeling to fully automated classification. It also supports content- and context-based classification, helping organizations align protection policies with compliance and IP protection needs across mixed environments.
What it helps with:
- Building policy-driven protection using consistent labels
- Improving regulatory readiness through structured classification
Data Loss Prevention (DLP)
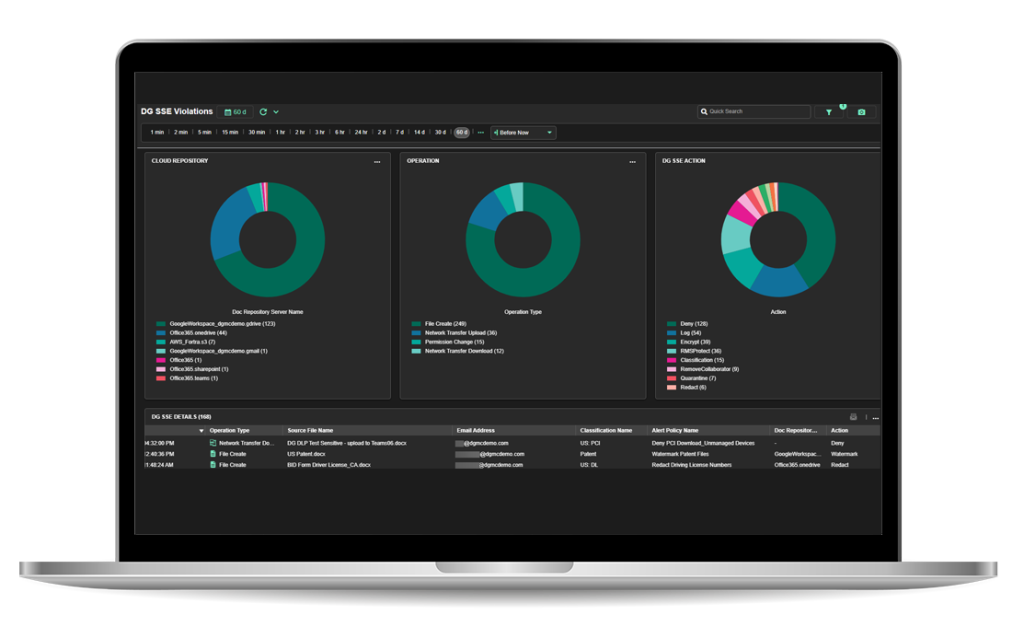
Fortra DLP is built to provide visibility into critical data and IP and help organizations understand and block data threats wherever data lives or moves—from endpoint to cloud. It includes endpoint coverage for preventing unsafe data egress even off-network, and centralized management tooling to build and manage sophisticated policies without deep technical overhead.
What it helps with:
- Immediate visibility into sensitive data patterns and movement
- Endpoint controls to reduce accidental or risky egress
- Centralized, policy-based management to speed deployment
Videos
-

Fortra® — We Break the Attack Chain
-

Take Control of Data Risk Across Every Environment
-

Boldon James - Data Classification Overview
-

DB2 Data and Beyond: How to Get Fast, Flexible Insights
-

Penetration Testing: Enabling security teams to conduct advanced testing with ease - HelpSystems
-

Fortra's Data Security Suite
-

Meet Fortra Your Cybersecurity Ally
-

Boldon James | SharePoint Classifier
Brand Protection
Fortra Brand Protection (Digital Risk Protection) helps organizations defend against external threats that target trust—detecting, analyzing, and stopping phishing, social media impersonation, and dark web threats, with monitoring across multiple digital channels and response workflows designed for fast mitigation.
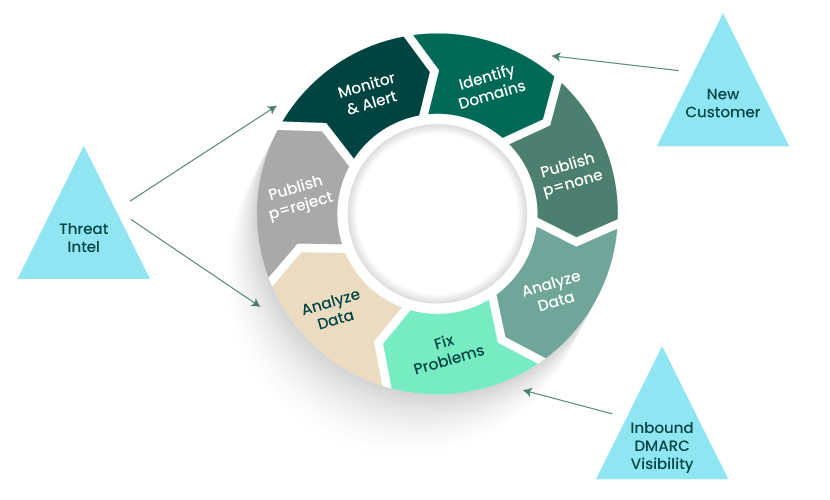
Domain Monitoring
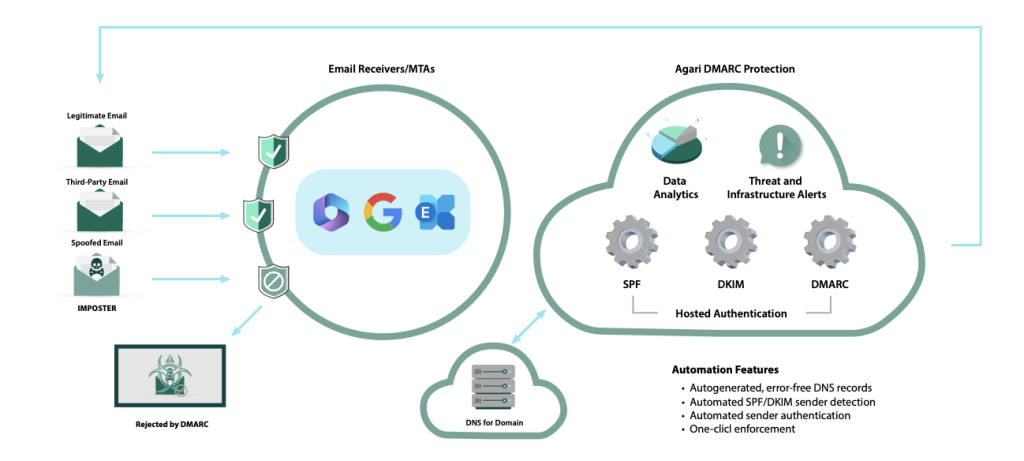
Domain Monitoring helps identify suspicious and look-alike domains by tracking signals like SSL certificate logs, passive DNS, and zone files across a large number of TLDs—supporting early detection of impersonation infrastructure. It can also be paired with DMARC-focused protections to strengthen defenses against domain-based phishing and spoofing.
What it helps with:
- Catching impersonation and look-alike domain activity early (
- Hardening domain trust with complementary email authentication strategies
Phishing Protection
Phishing Protection focuses on detecting phishing sites and campaigns and moving quickly to disruption through takedown operations. Fortra highlights automated mechanisms and an “always-on” approach aimed at minimizing the window of exposure, including coverage that can extend into attack types like smishing/vishing where relevant.
What it helps with:
- Faster disruption of credential phishing infrastructure
- Reducing end-user and customer exposure to impersonation-led fraud
Social Media Protection
Social Media Protection monitors for impersonation and abuse across the social landscape and supports response through platform-specific takedown playbooks and threat-focused workflows. It’s geared toward brands that need repeatable processes for handling fraudulent profiles, scam campaigns, and misuse of brand assets.
What it helps with:
- Detecting impersonation and brand misuse on social channels
- Streamlining mitigation through defined workflows and takedowns
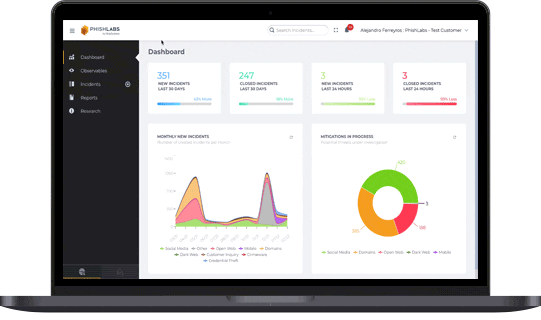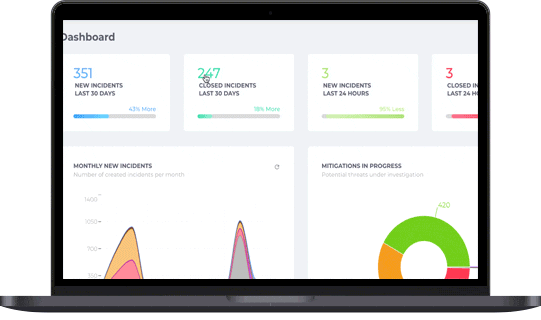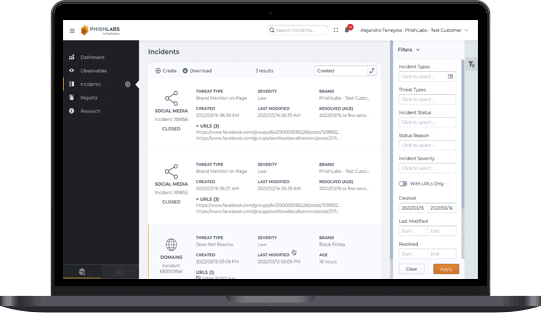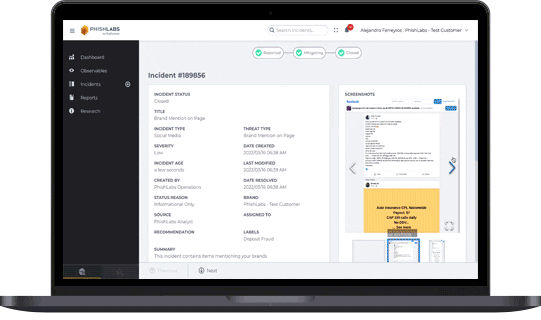
Dark Web Monitoring
Dark Web Monitoring combines automated detection with expert analysis to surface stolen credentials, leaked data, and relevant underground signals—supporting earlier intervention before threats translate into account takeover or broader fraud. Related monitoring can also focus specifically on compromised credentials across breaches and malware leak sources.
What it helps with:
- Early warning on credential exposure and brand-related underground chatter
- Faster investigation and response around compromised accounts

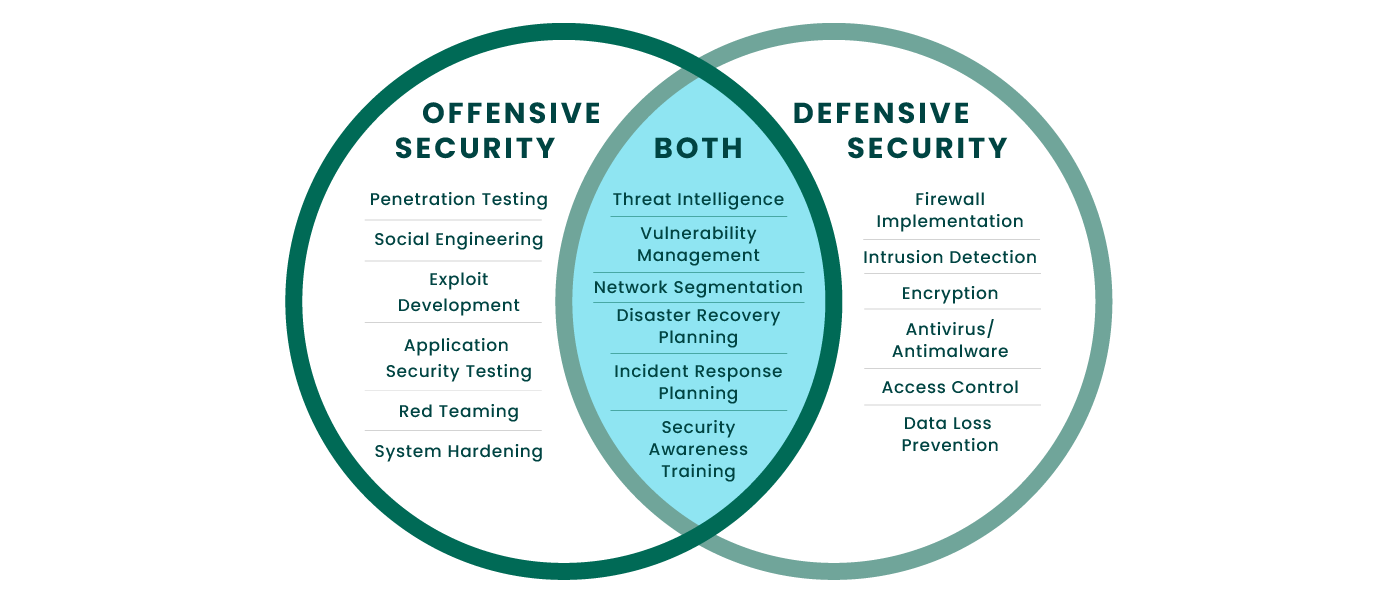
Offensive Security
Fortra Offensive Security helps organizations validate defenses through authorized testing—from penetration testing to red teaming—using toolsets that can interoperate during engagements (e.g., session passing/tunneling between capabilities).
Cobalt Strike
Cobalt Strike is an adversary simulation and red team platform used to replicate real attacker behaviors, including post-exploitation activity and covert communications, helping teams assess detection and response effectiveness in realistic scenarios.
What it helps with:
- Threat-representative emulation for security validation
- Red team operations designed to test controls under pressure
Core Impact
Core Impact is designed for automated penetration testing, simulating exploitation and lateral movement to validate real-world impact. It also highlights an exploit library curated and validated by in-house researchers, supporting repeatable testing aligned with remediation planning and reporting needs.
What it helps with:
- Validating exploit chains and movement paths safely
- Producing technical outputs that support remediation and compliance documentation
Outflank Security Tooling
Outflank Security Tooling is a specialized red team toolkit focused on stealth and evasion across key stages of an engagement, including payload and anti-forensic capabilities. It’s positioned to complement platforms like Core Impact and Cobalt Strike—enhancing realism for organizations testing against modern defensive stacks.
What it helps with:
- More realistic “under-the-radar” testing against modern EDR/AV
- Enhancing offensive assessments through compatible tooling





