Generative AI tools present both a significant opportunity and a genuine risk. While GenAI can enhance, streamline, and augment a wide range of workflows, it also introduces the potential for misuse and the exposure of sensitive or proprietary data. As a result, many organizations are struggling with GenAI adoption. GenAI is top-of-mind for many IT teams, and most are in the early stages of experimentation but lacking the governance, controls, and safeguards required to adopt GenAI safely.
Sophos Workspace Protection, provides all the controls organizations need to safely and easily embrace GenAI such as:
- Get visibility into the GenAI tools and services currently being used
- Easily setup policies to block unsanctioned GenAI sites, apps, and tools both in and out of the browser
- Optionally warn users against the use of unsanctioned services so they can self-govern
- Use data boundary controls to block, warn, or allow file uploads or downloads and copy and paste operations to prevent sensitive data mistakes
What You Need:
Safe GenAI policies are made possible thanks to a few of the key capabilities that make up Sophos Workspace Protection:
- Sophos Protected Browser integrates a secure web gateway with rich policy controls and data boundary controls that provide a transparent and familiar experience for workers
- Sophos DNS Protection for Endpoints adds an additional layer of domain-level security and control that spans across all ports, protocols, and apps on the device
- Sophos Central provides a consistent easy management experience with rich insights and reporting
These products integrate seamlessly to make safe GenAI adoption easy.
How it Works:
Watch this video for a quick demonstration of how it works, and how easy it is to set up:
One of the powerful but easy capabilities of the Sophos Protected Browser are the data boundary controls – which does what it says on the tin. It establishes boundaries around data operations such as copy and paste, upload and download, and more, to keep data within allowed applications where necessary, and prevent potentially costly data sharing mistakes:
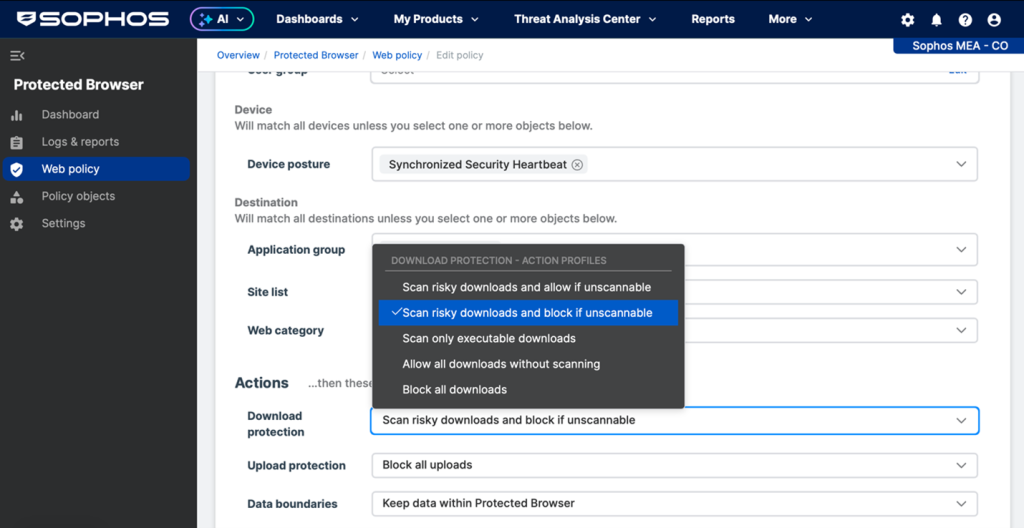
Sophos Protected Browser provides granular data boundary controls for uploads, downloads, copy and paste, and more.
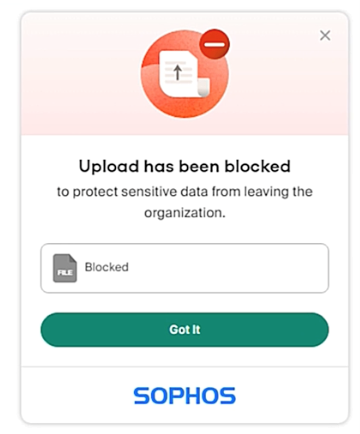
Users are notified when their actions are blocked.
Get a full overview of the data boundary control options in the online documentation.
Restricting Access Through Sophos Protected Browser Only:
For organizations looking to restrict all access to GenAI webservices through the Sophos Protected Browser only, this is also very possible when combined with Sophos Endpoint App Control which can block the use of all other browsers ensuring all interaction with GenAI is done through the Sophos Protected Browser.
Learn More about Sophos Workspace Protection:
Check out all the great capabilities and use cases for Sophos Workspace Protection and be sure to participate in the early access program for the new Sophos Protected Browser.
Source: Sophos






