Sophos’ latest annual study of the real-world ransomware experiences of retail organizations explores the full victim journey, from attack rate and root cause to operational impact and business outcomes.
This year’s report sheds light on new areas of study, including an exploration of ransom demands vs. ransom payments and how often retail organizations receive support from law enforcement bodies to remediate attacks.
Download the report to explore the full findings.
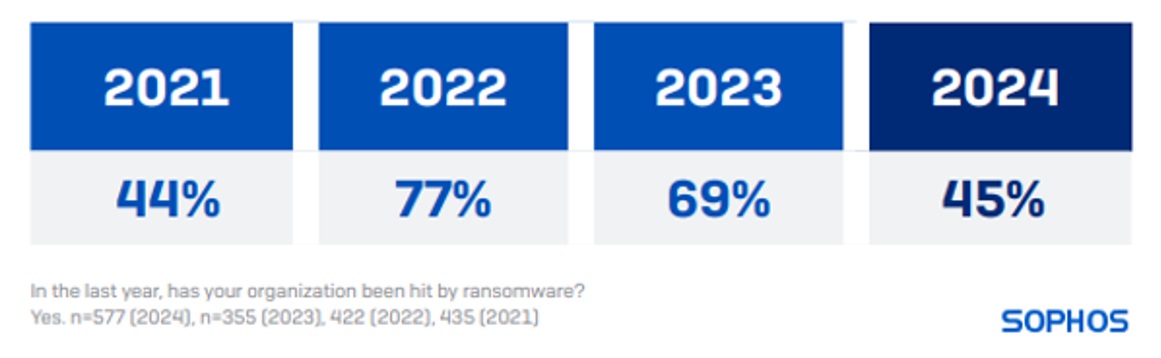
Attack rates have dropped, but recovery is more expensive
45% of retail organizations reported they were hit by ransomware last year. This is a notable and welcome drop from the 69% and 77% ransomware rates reported in 2023 and 2022, respectively.
92% of retail organizations hit by ransomware in the past year said that the cybercriminals attempted to compromise their backups during the attack. Of the attempts, 47% were successful.
56% of ransomware attacks on retail organizations resulted in data encryption, a considerable drop from the 71% reported in 2023 and 68% in 2022. The data encryption rate in retail was notably lower than the global cross-sector average of 70% and the lowest across all sectors other than financial services (49%).
Retail reported the second-highest data extortion rate (5%) jointly with financial services, where the data was not encrypted but they were held for ransom.
The mean cost for retail organizations to recover from a ransomware attack was $2.73M in 2024, an increase from the $1.85M reported in 2023.
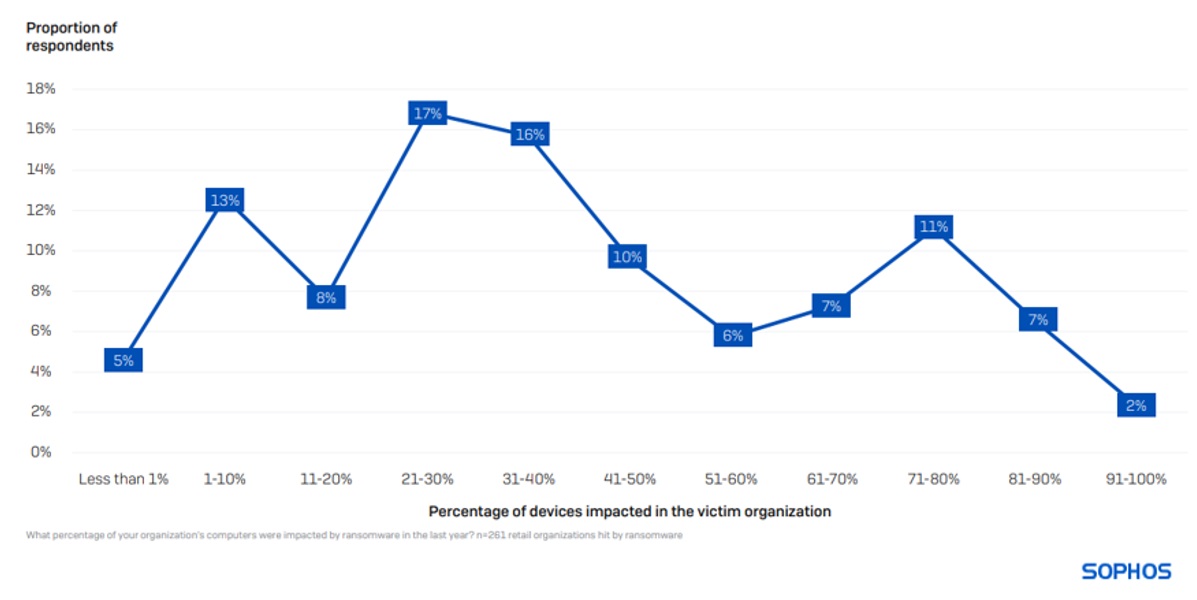
Devices impacted in a ransomware attack
On average, 40% of computers in retail are impacted by a ransomware attack. Having your full environment encrypted is extremely rare, with only 2% of organizations reporting that 91% or more of their devices were impacted.
Retail’s propensity to pay the ransom has increased
66% of retail organizations restored encrypted data using backups, while 60% paid the ransom to get data back. The use of backups in retail organizations has fallen slightly for the second consecutive year, but what is more concerning is the sector’s propensity to pay the ransom, which has increased considerably over the last year.
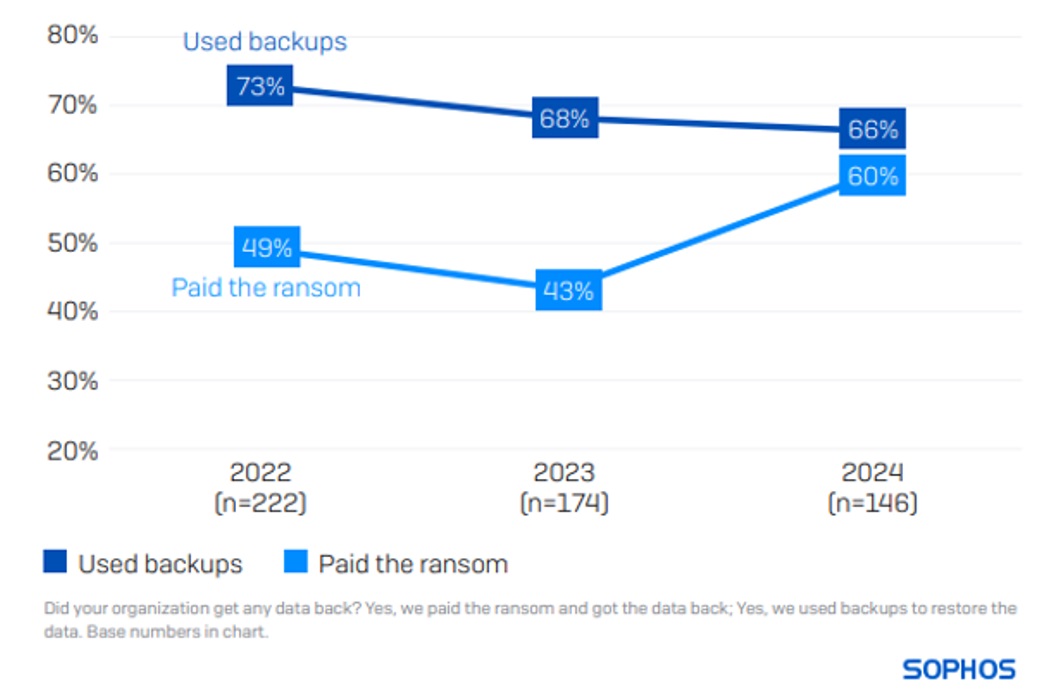
A notable change over the last year is the increase in the propensity for victims to use multiple approaches to recover encrypted data (e.g., paying the ransom and using backups). In this year’s study, over one-third of retail organizations (39%) that had data encrypted reported using more than one method, more than double the rate reported in 2023 (16%).
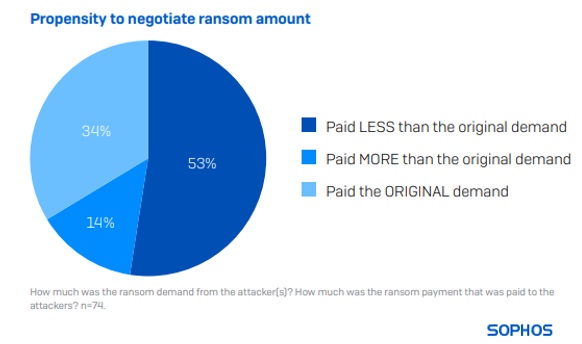
Retail victims rarely pay the initial ransom sum demanded
 78 retail respondents whose organizations paid the ransom shared the actual sum paid, revealing that the average (median) payment has decreased by 68% over the last year, from $3M to $950K.
78 retail respondents whose organizations paid the ransom shared the actual sum paid, revealing that the average (median) payment has decreased by 68% over the last year, from $3M to $950K.
Only one-third (34%) of respondents said that their payment matched the original request. 53% paid less than the original demand, while only 14% paid more.
Download the full report for more insights into ransom payments and many other areas.
About the survey
The report is based on the findings of an independent, vendor-agnostic survey commissioned by Sophos of 5,000 IT/cybersecurity leaders across 14 countries in the Americas, EMEA, and Asia Pacific, including 577 from the retail sector. All respondents represent organizations with between 100 and 5,000 employees. The survey was conducted by research specialist Vanson Bourne between January and February 2024, and participants were asked to respond based on their experiences over the previous year.
Source: Sophos






