The latest annual Sophos study of the real-world ransomware experiences of energy, oil/gas and utilities sector – a core element of the critical infrastructure supporting businesses – explores the full victim journey, from attack rate and root cause to operational impact and business outcomes.
This year’s report sheds light on new areas of study for the sector, including an exploration of ransom demands vs. ransom payments and how often energy, oil/gas and utilities organizations receive support from law enforcement bodies to remediate the attack.
Download the report to get the full findings.
Attack rates and recovery rates have remained steady
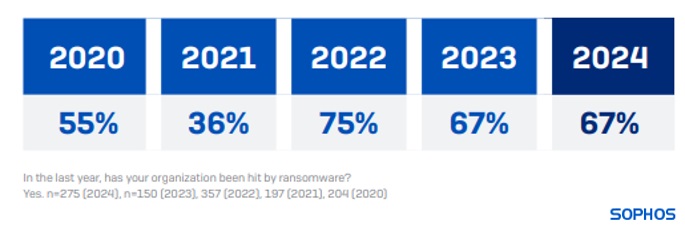
67% of energy, oil/gas and utilities organizations were hit by ransomware in 2024, identical to the attack rate reported in 2023.
98% of energy, oil/gas and utilities organizations hit by ransomware in the past year said that the cybercriminals attempted to compromise their backups during the attack. Four in five (79%) of these backup compromise attempts were successful, the highest rate of successful backup compromise across all sectors.
80% of ransomware attacks on energy, oil/gas and utilities organizations resulted in data encryption in 2024, in line with the encryption rate reported by this sector in 2023 (79%) but higher than the 2024 cross-sector average of 70%.
The mean cost in energy, oil/gas and utilities organizations to recover from a ransomware attack was $3.12M in 2024, similar to the $3.17M reported in 2023.
Devices impacted in a ransomware attack
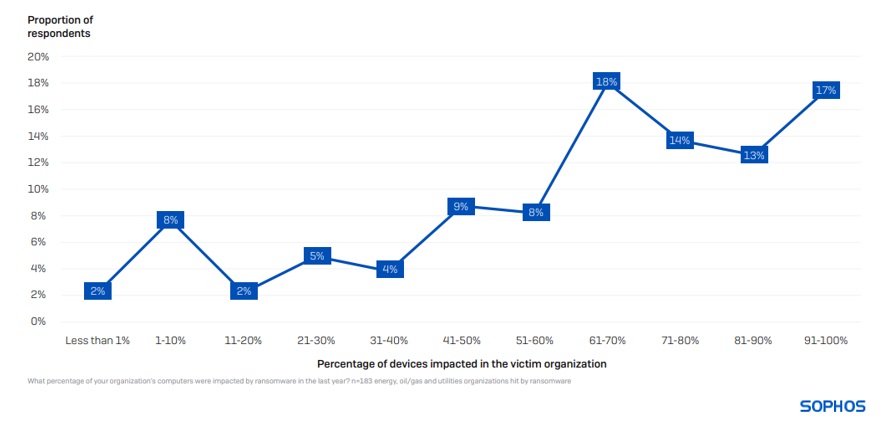
On average, 62% of computers in energy, oil/gas and utilities are impacted by a ransomware attack, considerably above the cross-sector average of 49%. Unlike other sectors where only a small percentage of organizations have their full environments encrypted, approximately one in five energy, oil/gas and utilities organizations (17%) reported that 91% or more of their devices were impacted.
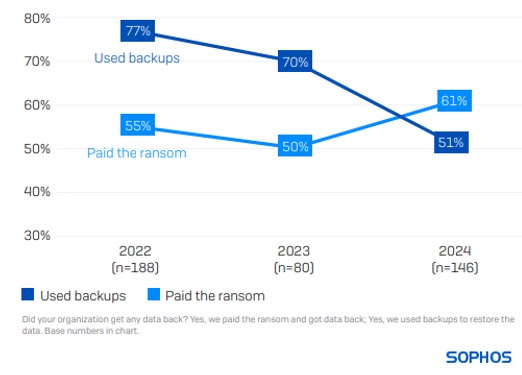
The propensity to use backups for data recovery has decreased
61% of energy, oil/gas and utilities organizations paid the ransom to get encrypted data back, whereas only 51% restored encrypted data using backups – the lowest rate of backup use reported across all sectors. This is the first time that energy, oil/gas and utilities organizations have reported a higher propensity to pay the ransom than use backups. In comparison, globally, 56% paid the ransom, and 68% used backups.
This year’s findings represent a marked change from the previous two years when the sector enjoyed impressive rates of backup use (70% in 2023 and 77% in 2022).
A notable change over the last year is the increase in the propensity for victims to use multiple approaches to recover encrypted data (e.g., paying the ransom and using backups). This time, 35% of energy, oil/gas and utilities organizations that had data encrypted reported using more than one method, higher than the 26% reported in 2023.
Critical Infrastructure victims don’t often pay the initial ransom sum demanded
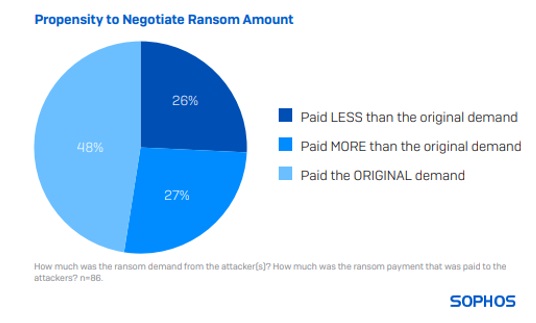
86 energy, oil/gas and utilities respondents whose organizations paid the ransom shared the actual sum paid, revealing that the average (median) payment was $2.5M in 2024.
A little less than half (48%) of respondents said their payment matched the original request. 26% paid less than the original demand, and 27% paid more.
Looking at the data by industry, energy, oil/gas and utilities has the highest propensity to pay the original ransom amount demanded by attackers. It is also the sector with the second lowest propensity to pay less than the original demand.
Download the full report for more insights into ransom payments and many other areas.
Source: Sophos






