Despite spending more than $18.5 billion on identity security products in 2024—a 15% increase year over year according to Gartner—identity remains the most common entry point for attackers. It’s the most used vector for initial compromise, and the trend is only expected to continue. This year alone, there have been over 800 million new sets of stolen credentials compromised as a result of the explosion of infostealers.
So, why are we still struggling?
The short answer is that identity security has not evolved fast enough. In contrast to other areas of cybersecurity, identity continues to be stuck in legacy thinking. Traditionally, it has been considered a function of compliance and business enablement, rather than a front-line security function. As a result, most organizations rely on fragmented tools, complex implementations, and reactive controls that are unable to keep up with modern threats.
Account compromise is not an anomaly, but an inevitable consequence of an outdated model.
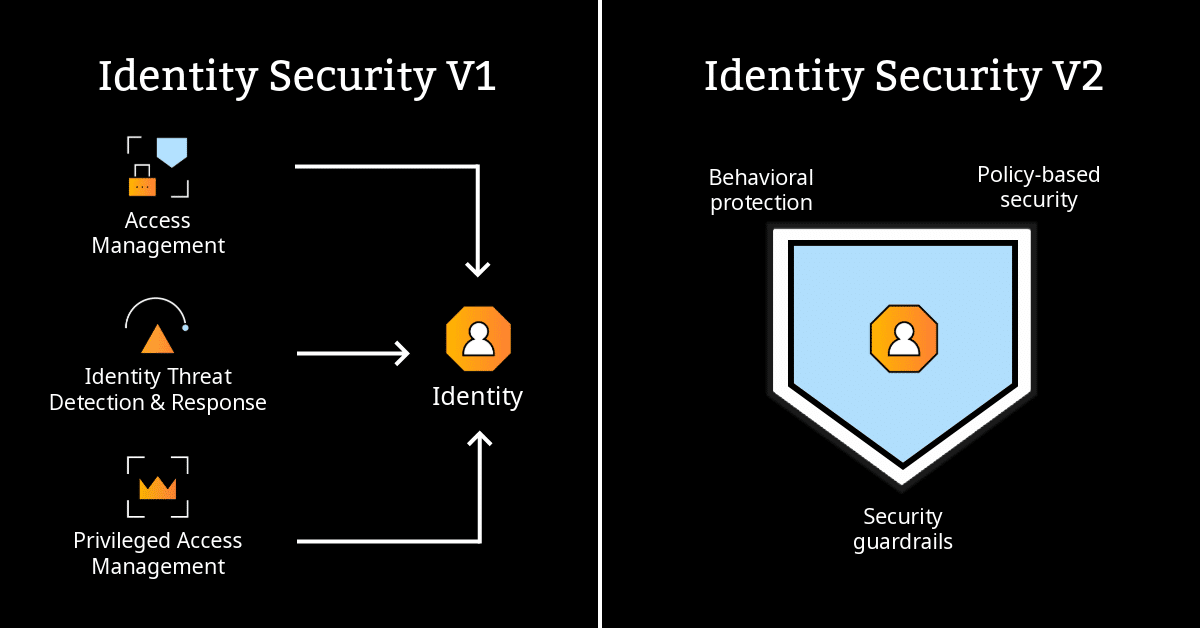
We’re still operating in what can only be called Identity Security v1. This is a first-generation approach that lacks the agility, integration, and focus necessary to combat today’s threats. The strategy is to layer controls over already exposed environments, often through projects that can take many years to complete. But attackers don’t wait—and neither should we.
A clear symptom of this lack of control is the uncomfortable conversations that many security leaders face: What is our residual risk? What does that mean in business terms? When will we be done? These questions are difficult to answer when you’re not fully in control and must constantly react to the environment as it changes beneath you.
Imagine a state where you can clearly define and enforce foundational identity controls: every admin is required to authenticate with MFA, service accounts are restricted to their usual, approved behavior, and all access is denied by default unless explicitly allowed. These controls aren’t aspirational: they’re implementable, enforceable and, most importantly, measurable. Their effectiveness is reflected in the threats that are blocked or contained before they can escalate, providing a direct line between control and risk reduction.
What is needed is a shift in both mindset and technology. Identity Security v2 puts compromise prevention at the centre. It is proactive, universal, and built to manage identity risk without getting in the way of business. As a result, identity is not treated as an afterthought, but as a control point.
There is an urgent need for this change. A perfect storm is brewing around outdated assumptions about identity’s role in security, a lack of modern tools that provide real-time control, and growing complexity across cloud, SaaS, and hybrid environments. Together, these forces call for a new approach, one that allows us to control now, everywhere it matters, and fine-tune later.
We cannot afford to wait. The cost of inaction is written clearly in breach reports and stolen credentials are piling up by the day.
Why identity is different and why that matters
Identity stands apart from other areas of security. Unlike most security domains, identity is fundamentally about people. Even non-human identities, service accounts, APIs, and machine identities ultimately reflect human decisions made by either developers, admins, or platform owners.
Identities are unique in that they are woven tightly into the day-to-day activities of an organization. It affects how people access tools, collaborate, and accomplish tasks—and, crucially, how they feel while doing so.
Identity has historically been funded for two reasons:
- How can we quickly onboard new joiners and make authentication seamless for everyone?
- How can we meet compliance requirements and avoid costly violations?
Now, a third and fundamentally different driver has emerged: how can we defend against identity-based threats? It requires new skills and a new mindset that may not always be aligned with traditional efficiency or compliance objectives.
In many cases, efficiency is associated with an increase in risk and over-provisioned access is a common consequence. The scope of compliance is narrow and deep, whereas security requires broad, real-time visibility and control. Due to these competing priorities, identity teams need to evolve into identity security teams with a new mandate and dedicated tools.
In most areas of security, this evolution is already well established: network, endpoint, and cloud teams all work alongside their specialized security counterparts, supported by purpose-built tools. But in identity, that model is often missing. Teams managing systems like Active Directory, Entra, or Okta are rarely partnered with dedicated security teams, who are themselves enabled by specialized technology. They often lack the tools required to take a truly security-first approach.
To meet today’s threats, that must change.
Why today’s identity security tools are not enough
As identity security has not evolved organizationally, technology has also lagged—especially when compared to other security disciplines.
Let’s take network security as an example. Modern tools don’t just offer visibility; they serve as a universal control plane that enforces guardrails across the entire environment. Security teams can proactively define and apply security policies to control risk and respond in real time to threats. These controls are consistently applied, ensuring no part of the network operates outside the organization’s security framework.
Identity has not had the same evolution.
Today’s identity security tools fall into one of three categories:
- Tools that treat identity as a set of vulnerabilities to be remediated (e.g., weak passwords, excessive privilege, orphaned accounts)
- Tools that isolate risky accounts (e.g., vaulting via PAM)
- Tools that attempt to detect identity-based threats and respond (e.g., ITDR)
The solutions are fragmented, focusing only on cloud, SaaS, or native identity platforms, and are often implemented in silos. As a result, attackers can exploit these gaps easily.
More critically, these tools do not empower identity security teams to take control of risk. They keep teams reactive, forcing them to chase down threats, remediating after the fact, and layering controls in response to what has already happened.
In today’s more complex environments, that model simply does not work. Treating identity as a list of backlog items to fix means exposure persists until everything is perfectly remediated, which is something no organization can realistically achieve.
It is possible to reduce exposure by locking down high-risk accounts; however, this is typically a difficult process, degrades the user experience, and does not scale well. This approach demands perfection: perfect visibility, perfect execution, and complete coverage across every critical system. No company can honestly claim they have achieved that.
Solving account compromises requires more than a patchwork. It requires a new kind of identity security technology—one that gives teams real control, closes gaps proactively, and puts you in the driver’s seat.
How do we take control?
Authentication today is not designed with security as the primary goal. When designing networks, security is front and center. Firewalls, segmentation, and controls are built to limit blast radius and contain threats. You would not accept a network without built-in security controls. Yet authentication is typically designed to ensure uptime and availability. The priority is operational: will users be able to log in when needed? Will the systems stay up and running to support the business? This mindset reflects identity’s legacy as a business enabler, not a security control.
But why is authentication not built security-first?
Why don’t we start from a position of denying by default and applying security controls to enforce security standards in line with our risk appetite? As a result, the blast radius will be narrowed, and the risk of account compromise will be reduced.
Imagine if these were the default policies:
- Require MFA for all access to sensitive infrastructure
- Deny any connection not originating from trusted sources
- Block authentication using legacy or insecure protocols
When we approach identity with this mindset, the game changes. Security risks become less urgent because the environment is controlled by design. It is now easier to explain risk to executives, not because the problems have disappeared, but because we have taken charge of how identity is protected.
This gives you the space and time that you need to modernize your identity landscape while staying in control of risk every step of the way—whether that’s adopting ephemeral credentials, moving toward zero standing privilege, or rethinking how access is granted.
Source: Silverfort