Power & Environmental Monitoring for Data Centre Racks
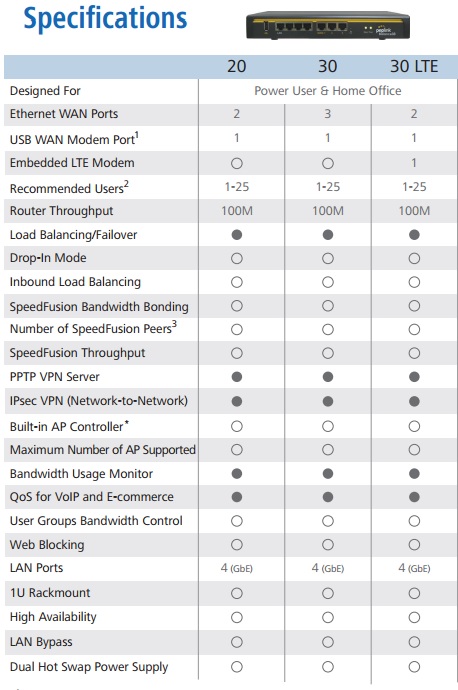
iMeter can monitor up to 496 of the following sensors from a single IP address: Current (Amps) using our unique intelliAmp® current sensor (pictured above) Voltage Temperature Humidity Airflow Water Leak Security (door contact or motion) Smoke The unique combination of the sensors on offer means that IT and Facilities personnel can analyse the […]
Power & Environmental Monitoring for Data Centre Racks Read More »