TLS is a popular Internet security protocol designed to establish secure communications that provides both privacy and data security. TLS was first developed by the Internet Engineering Task Force (IETF) with the first version being published in 1999.
TLS was created from another encryption protocol called Secure Sockets Layer, or SSL. Since both protocols are so closely related, you may hear others use SSL and TLS interchangeably to describe secure communications over the Internet.
Ports 587, 2525, and 465 are commonly used to establish secure connections, but which you use varies based on whether you’re using IMAP or POP3 to access emails from your server. Your system administrator can also set specific ports for encryption on mail servers and other applications.
What is STARTTLS?
STARTTLS is a protocol command used to prompt an email server that the client wishes to upgrade the connection from an insecure connection to a secure one. STARTTLS can take an insecure connection and make it secure via TLS protocol. Having this option enabled on your mail server allows a secure connection to be established before any emails are sent.
How does TLS protect email communications?
TLS plays a role in protecting email communications by establishing a secure and encrypted connection between two points. TLS utilizes asymmetric encryption to keep email communications private and untampered with while in transit. In other words, using encryption for emails ensures that the contents of the message cannot be read or modified while being sent and provides a mechanism for authentication between the sender and recipient.
Emails that use SMTP risk having their messages compromised by man-in-the-middle attacks or wiretaps if they are operating without encryption. These attacks can silently copy your emails and read their contents or even change the contents of the message while it’s in transit. This not only compromises the integrity of the email, but can provide valuable information to attackers who are capable of launching even more sophisticated attacks against your domain, such as spear phishing or whaling campaigns.
Secure connections are established using a series of steps known as a “TLS handshake”. This handshake requires two parties in order to create a secure connection. When a message is sent using TLS, the handshake process gets into motion as follows:
- During the first phase, the client and server will specify which version of TLS they will use for the session.
- Then the client and server will pick which cipher suit they will use.
- The identity of the server will then be authenticated using the server’s TLS certificate.
- Finally, session keys will be generated and used to encrypt the email messages once the handshake is completed.
How to check if an email is using TLS
Today, close to 90% of emails both sent and received are encrypted. But how can you check for yourself?
Server administrators should be able to verify their email server is using some form of encryption by checking their certificate store and validating that their certificate is both installed correctly and up to date.
If you’re simply checking an email, you can verify if the message was sent using encryption by checking the headers of the message. In Gmail, this can be done by opening the email in question and clicking on the small arrow next to your name underneath the sender’s address.
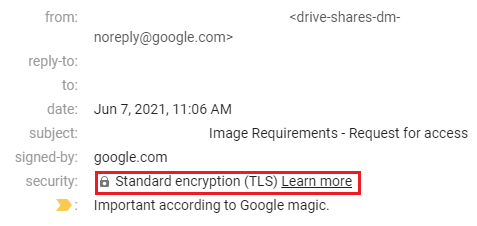
This can be done in Microsoft Outlook as well by opening the email you wish to check, and then navigating to File > Properties. This will open up the email header information which will contain any TLS information if available.
Is TLS the only protection I need?
TLS plays a vital role in email security, but it can’t protect against all email-based threats. Emails using encryption are protected against:
- Man-in-the-middle attacks
- Messages read or eavesdropped on by attackers while in transit
- Messages being forwarded to attackers
However, TLS cannot protect emails against:
- Phishing attempts using lookalike domains
- Malicious attachments that contain viruses
- Links inside of emails that redirect to phishing sites
- Emails that use social engineering to trick recipients into sharing sensitive information
- Servers sending spoof emails from domains that they do not control or defend
The Agari Advantage
Agari’s Email Security solutions utilize TLS and DMARC to ensure that emails are encrypted, as well as protected against phishing attacks from domain spoofing. Phishing attacks that use lookalike domains trick unsuspecting recipients into clicking links or sending sensitive information by pretending to be a trusted sender. These attacks can occur directly over a secure connection since they don’t have to abuse a lack of encryption to succeed.
By combining TLS encryption, organizations can deploy a security strategy that stops email-based attacks at all levels. For email protection beyond TLS, watch Agari’s Phishing Defense simulated product tour to see it in action for yourself!
Source: HelpSystems





