Hackers have a deep playbook for penetrating networks. Even when managed service providers (MSPs) provide their clients with a robust defense, malicious actors can still infiltrate systems to launch ransomware or other attacks.
Small and medium-sized businesses (SMBs) look to MSPs for help because they can’t protect themselves in the face of mounting threats. For example, a recent study showed that ransomware attacks have nearly doubled since 2020, just one of many attack vectors that can severely impact company operations.
While MSPs are increasingly well-versed in cybersecurity measures, they can become overwhelmed. Software tools such as antivirus (AV) and endpoint detection and response (EDR) help them to detect when security issues arise. However, many MSPs do not have the necessary capabilities to carry out threat hunting and incident response for digital forensics investigations and analyzing malware.
Highly trained cybersecurity professionals with the skills to provide advanced threat protection (ATP) are expensive to hire and in high demand. The vast majority of MSPs are not in the position to build up a massive ATP infrastructure and team, but they do have a quality option: managed detection and response (MDR).
Also known as a managed security operations center (SOC), or MDR, managed SOC provides the highest level of threat protection to MSPs and their clients. It combines technology solutions with expert human teams for advanced threat hunting, monitoring and incident response. Armed with MDR, MSPs can identify threats and quickly limit their impact without having to add costly additional staff.
What is MDR? A cybersecurity necessity
The role of managed SOC, or MDR, solutions has evolved significantly in an MSP’s practice. For an increasingly large proportion of SMB clients, MDR has gone from a nice-to-have to a necessity.
This shift is reflected in the core tenets of the NIST cybersecurity framework, a set of interconnected steps for managing risk to critical infrastructure. They are:
- Identify
- Protect
- Detect
- Respond
- Recover
Most organizations today – MSPs, small businesses, IT departments – spend 85% of their budget on “protect”, leaving only a small portion to spend on the other four phases. However, there is a growing awareness that a change in cybersecurity investment is now needed. The leading research firm Gartner recently observed:
“IT risk and security leaders must move from trying to prevent every threat and acknowledge that perfect protection is not achievable. Organizations need to detect and respond to malicious behaviors and incidents, because even the best preventative controls will not prevent all incidents.”
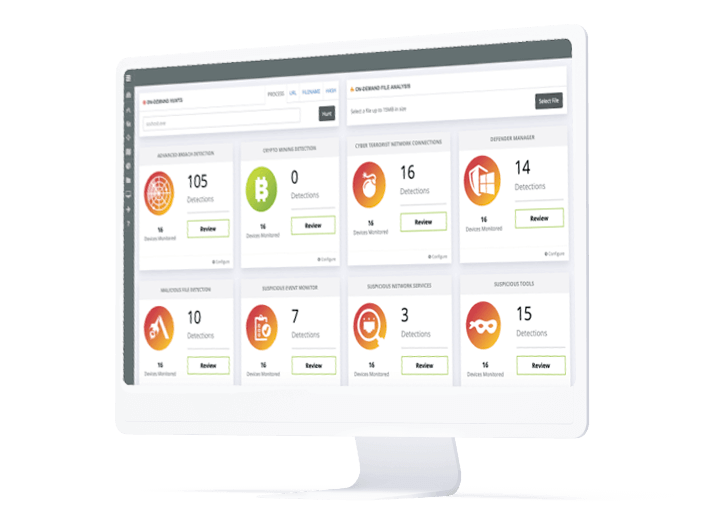
Adding MDR and managed SOC are how MSPs address this reality. For example, protection measures such as AV and firewall may detect malicious files, but additional security must now go far beyond that.
That’s because hackers are increasingly using techniques to infiltrate networks that do not appear malicious on the surface, allowing them to evade defenses. Once a hacker has entered an SMB’s network with this technique, they can dwell unseen in the system, gathering critical information before they strike.
For instance, bad actors know that they can use a normal tool like the Windows PowerShell command-line interface (CLI) for abnormal activities. Working from PowerShell, a hacker can then pull the Mimikatz open-source application to watch for and harvest authentication credentials as packets move through the system. AV software won’t register something like that as a malicious act, but it’s certainly a suspicious one, especially if the commands are originating from a hostile nation.
MDR helps MSPs to spot bad behaviors that get past AV and other traditional protective measures. With a solution like Datto Managed SOC in place, MSPs are alerted of these hidden compromises so they can find, contain and neutralize such an attack before it becomes a major problem.
Better economics
From a security standpoint, MDR makes sense, especially as ransomware gangs and other bad actors become increasingly sophisticated.
Outsourcing MDR to a managed SOC is also the right budgetary choice for an MSP – and often the only feasible option. That’s because building a SOC from the ground up in-house is prohibitively expensive. Without even accounting for the technology infrastructure, the staffing costs can be staggering. In order to run 24/7 a SOC needs at least three expert security analysts, but it reasonably requires several more than that.
However, skilled MDR professionals are in high demand now and are commanding equally high salaries. That leads to a Catch-22 for MSPs who are considering homegrown MDR services: Do you invest heavily in setting up your in-house SOC first and then try and get the clients? Or do you sell clients on it and then try to build up the staff and services to keep your promises? It’s an expensive risk on the one hand, a reputational risk on the other.
The more sensible path for MSPs is to white label their MDR by outsourcing a managed SOC service. That’s how MSPs are responding to this growing need in the market, in a way that they couldn’t do otherwise.
The role of remediation
With MDR in place via a managed SOC, MSPs can go on the offensive by detecting and containing security threats before they spread. This threat hunting is key to cybersecurity remediation, which is the process of identifying and fixing IT security problems. Remediation also involves resolving any issues that might have arisen after a breach.
 Threat hunting is a more mature security activity requiring deep experience in forensics and incident response – initiatives that most MSPs lack the people, training and tools to undertake. The operations of more and more SMBs are transitioning to digital infrastructure, however, meaning that anyone can become a target. That’s because any kind of customer information today has value, so it can be stolen and resold on the dark web.
Threat hunting is a more mature security activity requiring deep experience in forensics and incident response – initiatives that most MSPs lack the people, training and tools to undertake. The operations of more and more SMBs are transitioning to digital infrastructure, however, meaning that anyone can become a target. That’s because any kind of customer information today has value, so it can be stolen and resold on the dark web.
When an MSP offers MDR, cybersecurity becomes proactive. Managed SOC experts are trained to root out bad actors that have infiltrated SMB endpoints and networks and contain those threats. As discussed above, that goes beyond negating the likes of malware, ransomware, distributed denial of service (DDOS) attacks, and phishing: MDR professionals recognize seemingly normal activities that can devastate a business if left unchecked.
Managed SOC is MDR: How to find the right provider
The right MDR ensures that MSPs can instantly extend their team to include world-class personnel who are experts in 24×7 threat monitoring.
MSPs should look for a managed SOC that protects clients across their entire infrastructure including endpoints, networks and the cloud. Efficient log monitoring, threat intelligence and hunting, breach detection, intrusion monitoring, advanced malware prevention, and PSA ticketing should all be included. These features are essential for comprehensive protection and effective remediation that won’t tax MSP personnel.
Improve your security offerings and experience the confidence that comes with continuous protection against attackers. Schedule a demo of Datto Managed SOC.
Source: Datto




