NSS provides end-to-end cybersecurity services to strengthen your organization’s security posture. Our Training & Certification Services empower your team with the knowledge and skills to tackle evolving threats. Our Vulnerability Assessment & Management services help identify, prioritize, and mitigate security risks before they become critical. With Penetration Testing, we proactively uncover and address vulnerabilities before attackers can exploit them.
Beyond security assessments, NSS offers Implementation Support Services to optimize performance, accelerate growth, minimize risks, and fortify your business framework. Additionally, our Presales Consulting Services guide businesses in selecting the most effective, tailored cybersecurity solutions to meet their unique needs.
Training & Certification Services
Click HereVulnerability Assessment & Management
Click HerePenetration Testing Services
Click HereImplementation Support Services
Click HerePresales Consulting Services
Click Here



Sophos Managed Detection and Response (MDR) is a comprehensive cybersecurity service designed to protect organizations from advanced threats. By integrating with various technologies, including Google Workspace, Sophos MDR offers 24/7 monitoring and rapid response to potential security incidents.
Sophos MDR has been recognized as the top-rated MDR service by G2 Peer Reviews, reflecting its effectiveness and user satisfaction.
In addition, Sophos has been named a Leader in the 2024 IDC MarketScape for Worldwide Modern Endpoint Security for Midsize Businesses, highlighting its strong position in the cybersecurity market.
For organizations seeking robust protection against cyber threats, Sophos MDR provides a reliable and effective solution.

Sophos Rapid Response is a 24/7 service designed to assist organizations during cybersecurity incidents. It offers immediate support to identify, contain, and remediate threats, minimizing potential damage and downtime. Sophos Rapid Response is available 24/7/365, including over the holiday period.
A comprehensive evaluation by 451 Research, a global research and advisory firm, has highlighted the effectiveness of Sophos Rapid Response. The report underscores the service’s ability to swiftly detect and mitigate threats, providing organizations with the expertise and resources needed to respond effectively to security incidents.
In addition to its core services, Sophos Rapid Response collaborates with other Sophos solutions to enhance overall security posture. For instance, the integration with Capsule8 technology has expanded its capabilities, offering new Linux telemetry and event information to better detect and respond to threats.
By leveraging Sophos Rapid Response, organizations can benefit from expert guidance and support during critical security events, ensuring a swift and effective response to minimize potential impacts.

Sophos, a global leader in cybersecurity, has unveiled a new service called the Incident Response Services Retainer, which provides businesses with quick access to expert teams during cyber incidents. This service is available to both existing and new customers of Sophos, offering a fixed-cost model that simplifies the process of dealing with cyber threats.
The retainer includes proactive services like external vulnerability scanning and critical preparedness guidance, which help organizations bolster their security by identifying and addressing potential risks. Sophos’ analysis reveals a troubling trend: the median dwell time for ransomware attacks has decreased significantly, from nine days in 2022 to five in the first half of 2023, with attackers breaching critical systems like Active Directory in as little as 16 hours.
The service is designed to eliminate bureaucratic delays, enabling incident response teams to engage immediately during attacks, minimizing potential business disruption. Furthermore, the service supports compliance with directives like the NIS 2 Directive, ensuring organizations report major incidents within 24 hours. By providing rapid incident response capabilities, Sophos helps organizations safeguard their operations and data against evolving cyber threats.

Sophos Managed Risk, powered by Tenable, is a comprehensive service that combines Tenable’s vulnerability management technology with Sophos’ threat expertise. This fully managed service helps organizations identify and mitigate blind spots, providing clear insights into and prioritization of high-risk exposures. By leveraging Tenable’s extensive vulnerability coverage and risk-based prioritization, Sophos Managed Risk enables proactive management of attack surfaces, ensuring continuous monitoring and prompt notification of critical vulnerabilities. This collaboration between Sophos and Tenable addresses urgent security challenges, allowing organizations to effectively manage exposure risks and reduce the likelihood of costly breaches.

Sophos ZTNA, Zero Trust Network Access, is a security solution designed to enhance remote access by implementing a zero-trust model. Unlike traditional VPNs, which grant users broad access to corporate networks, ZTNA ensures that every user, device, and application is continuously authenticated and authorized before accessing specific resources. This approach significantly reduces the risk of unauthorized access and lateral movement within the network.
Sophos ZTNA offers several key benefits:
- Enhanced Security: By eliminating implicit trust, ZTNA ensures that only authenticated and authorized entities can access network resources, thereby reducing the attack surface.
- Scalability: ZTNA is designed to scale efficiently, accommodating the growing number of remote workers and devices without compromising performance.
- Simplified Management: Integrated with the Sophos Central console, ZTNA allows for centralized management, streamlining administrative tasks and reducing complexity.
- Seamless User Experience: ZTNA provides transparent, clientless access to web-based applications, ensuring a smooth experience for end-users.
In summary, Sophos ZTNA offers a robust and scalable solution for organizations seeking to secure remote access in today’s dynamic work environment.

Sophos Endpoint Security offers comprehensive protection against a wide range of cyber threats, including ransomware, malware, exploits, and phishing attacks. Its advanced features, such as Intercept X, utilize artificial intelligence and machine learning to detect and prevent sophisticated attacks before they impact systems. Sophos Central provides a unified management console, enabling organizations to efficiently oversee their security operations. Recognized as a leader in endpoint protection, Sophos has been named a Leader in the 2024 IDC MarketScape for Worldwide Modern Endpoint Security for Midsize Businesses.
In addition, Sophos Intercept X has been awarded “Best Endpoint Security” multiple times, underscoring its effectiveness in safeguarding against advanced threats.
For organizations seeking robust endpoint security solutions, Sophos provides a reliable and effective option to protect against evolving cyber threats.

Sophos Firewall is a leading network security solution designed to protect organizations from evolving cyber threats. It offers advanced threat protection, VPN capabilities, and centralized management for effective monitoring. With integrated deep packet inspection and AI-driven security, Sophos ensures comprehensive defense against malware, ransomware, and phishing attacks. Its seamless integration with other Sophos products strengthens security infrastructure, providing businesses with a reliable solution for safeguarding data and maintaining operational continuity.
Sophos Firewall has been recognized for its excellence in network security. It was named the best network security solution by CRN® and was acknowledged as a strong performer in The Forrester Wave™: Enterprise Firewalls, Q4 2022. Additionally, G2 users rated Sophos Firewall as the #1 firewall solution in their spring 2023 reports.
In January 2024, Sophos announced that its Managed Detection and Response (MDR) service now protects over 26,000 organizations globally, highlighting the increasing demand for proactive, expert-led security solutions.

Sophos, a global leader in cybersecurity, has enhanced its Network Detection and Response (NDR) capabilities by acquiring Braintrace, an innovator in NDR technology. Braintrace’s NDR provides deep visibility into network traffic patterns, including encrypted traffic, without the need for Man-in-the-Middle (MitM) decryption. This acquisition enables Sophos to integrate Braintrace’s technology into its Managed Threat Response (MTR), Rapid Response, and Extended Detection and Response (XDR) solutions, enhancing threat detection and response across its cybersecurity ecosystem. The integration offers defenders an ‘air traffic control system’ that sees all network activity, reveals unknown and unprotected assets, and exposes evasive malware more reliably than Intrusion Protection Systems (IPS). Sophos plans to introduce Braintrace’s NDR technology for MTR and XDR in the first half of 2022.

Sophos Server Workload Protection offers robust security for servers and containers across on-premises, data center, and cloud environments. By leveraging advanced threat intelligence, AI, and machine learning from SophosLabs and SophosAI, it provides comprehensive protection against ransomware, malware, exploits, phishing, and other cyberattacks. This solution ensures complete visibility into host and container workloads, identifying and mitigating threats before they can cause harm. Sophos Server Workload Protection is part of a broader cybersecurity portfolio that includes endpoint protection, firewall solutions, and managed detection and response services, all managed through the centralized Sophos Central platform.

Sophos Cloud Native Security is a comprehensive solution designed to protect workloads across various environments, including on-premises, data centers, and the cloud. It offers a unified platform that integrates multiple security features, ensuring robust protection against a wide range of cyber threats. This integration simplifies management and enhances visibility, allowing organizations to effectively monitor and secure their IT infrastructure.
The platform’s scalability and flexibility make it suitable for organizations of all sizes, adapting to their specific security needs. By leveraging advanced technologies and threat intelligence, Sophos Cloud Native Security provides proactive defense mechanisms, reducing the risk of data breaches and other security incidents. Its cloud-native architecture ensures seamless updates and continuous improvement, keeping pace with the evolving cybersecurity landscape.
In summary, Sophos Cloud Native Security delivers a robust, integrated, and scalable security solution that empowers organizations to protect their digital assets effectively in today’s complex threat environment.

Sophos Intercept X is a cutting-edge endpoint security solution designed to protect against zero-day threats and advanced cyberattacks. By leveraging signatureless anti-exploit, anti-ransomware, and anti-hacker technologies, it offers comprehensive protection without relying on traditional file scanning or signature updates. This approach ensures that even unknown threats are detected and neutralized promptly.
In addition to its advanced threat detection capabilities, Sophos Intercept X provides automated forensic reporting, tracing attacks back to their origins and offering guidance to strengthen an organization’s security posture. Its deep-cleaning technology effectively removes deeply embedded malware, ensuring thorough remediation.
Sophos Intercept X is managed through the Sophos Central Admin console, providing a unified platform for security management. This integration allows organizations to efficiently monitor and respond to threats, enhancing overall cybersecurity resilience.

Sophos Email Security is part of Sophos’ broader cybersecurity offerings designed to protect organizations from modern email-based threats such as phishing, malware, and business email compromise (BEC). The service uses advanced AI to detect and block malicious emails before they reach their target. Sophos also integrates automated response capabilities to mitigate these threats. By combining these features, Sophos Email Security helps prevent data breaches and financial losses while offering enhanced visibility and control over email communications.

Sophos, a leading cybersecurity company, offers a comprehensive suite of Web Security solutions designed to protect organizations from a wide range of cyber threats. Their offerings include advanced malware protection, web filtering, and intrusion prevention systems, all managed through a centralized platform. This integrated approach ensures real-time threat detection and response, safeguarding sensitive data and maintaining business continuity. Sophos’ solutions are tailored to meet the needs of businesses of all sizes, providing robust security measures against evolving cyber threats.

Sophos Web Server Protection offers enhanced security features for businesses against evolving cyber threats. It provides robust protection by monitoring and mitigating potential vulnerabilities in web servers. Through constant updates and comprehensive defense mechanisms, it ensures that data remains secure from attacks such as hacking and unauthorized access. As part of its broader cybersecurity suite, Sophos integrates cutting-edge AI technology and real-time threat detection to safeguard digital infrastructure.

Sophos Mobile Security is a leading mobile threat defense application that operates on both Android and iOS devices. It offers comprehensive protection against various cyber threats, including malware, phishing, and ransomware. The app features an OS Advisor that alerts users when their devices are behind on updates, ensuring they stay protected with the latest security patches. Additionally, the Authenticator manages one-time passwords for two-factor authentication, enhancing account security. Sophos Mobile Security integrates seamlessly with Microsoft Intune, providing a unified approach to device management and security. This integration allows organizations to enforce security policies and manage devices efficiently, ensuring a robust defense against mobile threats.

Sophos offers a robust Intrusion Prevention System (IPS) designed to protect networks from unauthorized access and cyber threats. Integrated into their XG Firewall, this IPS provides real-time monitoring and automatic response to potential intrusions. It analyzes network traffic to detect and block malicious activities, ensuring comprehensive security for organizations.
In addition to the IPS, Sophos provides a range of security solutions, including malware protection, host intrusion prevention, and web security. These tools offer clear visibility into the security status of managed servers, allowing administrators to monitor and respond to threats effectively.
Sophos’ commitment to cybersecurity is evident in their continuous development of advanced security technologies, such as the Intercept X platform. This platform excels at blocking the latest threats, including ransomware and fileless attacks, providing organizations with a comprehensive defense against evolving cyber threats.
By integrating these advanced security measures, Sophos ensures that organizations can effectively defend against a wide range of cyber threats, maintaining the integrity and confidentiality of their networks and data.

Sophos Secure Data Lake is a centralized repository that aggregates critical information from EDR-enabled endpoints and servers, ensuring access to data even when devices are offline. This capability enhances event correlation, enabling rapid identification of suspicious activities across multiple devices. The Data Lake retains data for seven days by default, with an option to extend to 30 days for Sophos XDR users. To activate this feature, navigate to ‘Global Settings’ in the Sophos Central console, select ‘Data Lake uploads,’ and enable the ‘Upload to the Data Lake’ option. Currently, Sophos Data Lake supports Windows and Linux devices, with Mac support anticipated in the near future.

Sophos Remote Ethernet SD-WAN technology allows businesses to optimize their network performance and security by utilizing software-defined networking (SDN) capabilities. This solution enables businesses to connect remote sites, improving application performance and reducing latency. By incorporating intelligent routing, it ensures more reliable connectivity, security, and control over network traffic. Sophos SD-WAN is designed to help enterprises address the growing demand for flexibility and agility in their network infrastructures, while maintaining a high level of protection against evolving cyber threats.

Sophos Secure Switching is a comprehensive network security solution designed to enhance the performance and security of enterprise networks. By integrating advanced threat protection with seamless network management, it ensures that organizations can operate efficiently while maintaining robust security measures.
Key Features:
- Advanced Threat Protection: Sophos Secure Switching offers real-time threat detection and prevention, safeguarding networks against a wide range of cyber threats.
- Seamless Integration: The solution integrates smoothly with existing network infrastructures, providing a unified approach to network management and security.
- Scalability: Designed to grow with your organization, Sophos Secure Switching can be scaled to meet the demands of expanding networks.
- User-Friendly Management: With an intuitive interface, network administrators can easily configure and monitor network performance and security settings.
By adopting Sophos Secure Switching, organizations can achieve a balance between high network performance and stringent security requirements, ensuring a resilient and efficient network environment.

Sophos, a global leader in cybersecurity, has enhanced its Wireless Security offerings with the introduction of the APX Series Access Points. These devices integrate seamlessly with Sophos Central, enabling synchronized security across endpoints, mobile devices, and servers connected via Wi-Fi. This integration allows for real-time health status monitoring of connected devices, facilitating prompt responses to potential threats.
In addition to the APX Series, Sophos has expanded its Wi-Fi access point range by adding four new 802.11ac desktop and ceiling mount versions, as well as the AP 100X, a rugged 802.11ac model. These additions provide businesses with versatile and robust wireless solutions to meet diverse security needs.
Sophos’ commitment to innovation in wireless security underscores its dedication to providing comprehensive, integrated solutions that protect organizations from evolving cyber threats.

Sophos Centralized Encryption provides an efficient solution for securing data across organizations. This technology integrates with Sophos Central, offering centralized management for encryption policies and the protection of sensitive data across all devices. By using strong encryption standards, it ensures that information is accessible only by authorized individuals, reducing the risk of data breaches. The system is designed to be user-friendly, making it simple for administrators to deploy, monitor, and enforce encryption across various devices.

Sophos DNS Protection enhances cybersecurity by providing comprehensive web filtering and threat blocking. It secures businesses by preventing access to harmful sites and phishing attempts. Integrated with the broader Sophos ecosystem, DNS Protection offers automated threat detection, reducing the risk of data breaches. Sophos employs AI to improve security insights and streamline operations, ensuring swift and effective responses to emerging threats.

Sophos Phishing Threat Protection is a comprehensive security solution designed to safeguard organizations from phishing attacks. It uses advanced AI-driven threat detection, email filtering, and real-time URL analysis to block malicious links before they reach users.
With Sophos Email Security, organizations can prevent phishing attempts by analyzing email headers, body content, and attachments for suspicious elements. Additionally, Sophos integrates with endpoint security solutions like Intercept X to provide multi-layered protection, stopping phishing threats that bypass email defenses.
Another key feature is user awareness training through Sophos Phish Threat, which simulates phishing attacks and educates employees on recognizing and avoiding scams. By combining prevention, detection, and training, Sophos offers a robust defense against phishing threats.

FORTRA Vulnerability Management provides organizations with an advanced solution to identify and manage vulnerabilities across their networks. It offers proactive scanning, assessment, and prioritization of risks, helping businesses take timely action to protect against cyber threats. With tools designed for seamless integration and comprehensive threat intelligence, FORTRA enhances security resilience by automating key processes and focusing on critical vulnerabilities. Its adaptive system ensures organizations stay ahead of emerging risks, making it an essential part of any modern cybersecurity strategy.

Fortra’s Semi-Automatic Penetration Testing tools provide a robust solution for identifying vulnerabilities in an organization’s cybersecurity. These tools allow security teams to simulate realistic attack scenarios, uncover weaknesses, and address potential threats before attackers exploit them. By integrating automated scanning with manual testing, Fortra offers a hybrid approach that ensures comprehensive security assessments.
Key features include vulnerability management, penetration testing, and red teaming. Vulnerability management tools help identify and prioritize risks, ensuring timely remediation. Penetration testing mimics attacker behavior to assess an organization’s defenses, while red teaming evaluates an organization’s response to advanced, persistent threats.
With Fortra’s solutions, organizations can proactively identify security gaps, reduce risk, and improve their cybersecurity posture. By leveraging semi-automatic tools, security teams can save time, improve efficiency, and reduce the chance of human error during assessments. These tools are essential for maintaining compliance with industry standards and enhancing overall security resilience.
Fortra’s solutions are crucial for organizations looking to strengthen their defenses and stay ahead of cyber threats.

Cobalt Strike is a sophisticated threat emulation tool designed for adversary simulations and red team operations. It provides post-exploitation agents and covert channels, enabling security professionals to emulate advanced, stealthy threat actors within a network. Its malleable Command and Control (C2) framework allows customization of network indicators to mimic various malware strains, enhancing the realism of simulated attacks. Additionally, Cobalt Strike offers robust collaboration features, facilitating effective teamwork during security assessments.

The FORTRA Offensive Security Toolkit is an essential asset for enhancing cybersecurity measures. It is designed to assist organizations in assessing and defending their systems against cyber threats. This toolkit incorporates advanced techniques for penetration testing, vulnerability scanning, and real-time analysis. With the rise of sophisticated cyber-attacks, having such tools provides a strategic advantage in fortifying defenses. It is suitable for security professionals aiming to preemptively detect vulnerabilities, strengthen security protocols, and stay ahead of potential breaches.

Fortra’s Terranova Security offers comprehensive security awareness training to help organizations defend against evolving cyber threats, including those leveraging artificial intelligence (AI). Theo Zafirakos, Chief Information Security Officer at Fortra’s Terranova Security, emphasizes the importance of educating employees to recognize and mitigate AI-related security risks. He notes that hackers are increasingly using AI to develop sophisticated attacks, such as AI-generated phishing emails and malware designed to bypass detection. To counter these threats, Fortra’s training programs focus on enhancing employees’ ability to identify and respond to AI-driven cyberattacks. By incorporating AI into their training modules, organizations can better prepare their workforce to handle emerging security challenges.

Fortra’s Data Classification service helps organizations identify and protect sensitive information. With its robust categorization capabilities, it enables data to be labeled according to sensitivity, ensuring proper security protocols. Fortra’s solution provides automatic classification of both structured and unstructured data, assisting in compliance and reducing the risk of data breaches. Organizations can effectively manage their information security, making it easier to enforce data protection policies.

Fortra offers a comprehensive suite of Data Loss Prevention (DLP) solutions designed to protect sensitive information across various platforms. Their key products include:
- Clearswift Endpoint DLP: Provides real-time content inspection and adaptive redaction to prevent data breaches while maintaining workflow efficiency.
- Clearswift Secure Email Gateway: Protects against inbound cyberattacks and outbound data loss by analyzing email content and removing potential threats.
- Clearswift Secure Web Gateway: Ensures secure web traffic by enforcing consistent internet security policies, safeguarding data access and sharing.
- GoAnywhere MFT: Automates and encrypts secure file transfers between organizations and trading partners, protecting data during transit.
- Vera: Secures, tracks, and controls sensitive data shared externally, providing encryption and robust policy enforcement.
These solutions work seamlessly together, offering a robust defense against data loss, unauthorized access, and cyber threats. Fortra’s DLP offerings help businesses maintain compliance and secure their critical data.

FORTRA Managed File Transfer (MFT) is a secure, reliable solution designed for businesses to transfer files across systems and locations. It enhances collaboration while ensuring data security with compliance to industry standards. FORTRA MFT optimizes the management of file transfers by automating processes, reducing errors, and providing detailed tracking capabilities. Additionally, it integrates seamlessly with existing IT infrastructure, providing scalable solutions for diverse needs, from small businesses to enterprise-level organizations.

FORTRA’s DMARC, Domain-based Message Authentication, Reporting, and Conformance, Protection is a powerful tool to help organizations safeguard their email systems from phishing and spoofing attacks. By implementing DMARC, businesses can ensure that only authorized senders use their domain, preventing malicious actors from impersonating them. This advanced security measure strengthens email authentication, enhances trust, and improves deliverability rates. It also provides detailed reporting to track and analyze email traffic, ensuring comprehensive protection against evolving cyber threats.

FORTRA Digital Risk Protection offers cutting-edge solutions for safeguarding organizations from the growing cyber threat landscape. By providing comprehensive risk management, continuous monitoring, and advanced threat detection, it ensures that businesses remain protected against vulnerabilities and potential attacks. With a focus on proactive security, FORTRA’s services aim to mitigate risks and enable organizations to safely navigate the digital environment.

BeyondTrust’s Privileged Access Management, PAM, solutions offer comprehensive control over privileged accounts and users, enhancing cybersecurity by reducing risks associated with privileged credential misuse. Their portfolio includes tools like Password Safe, which automates password and session management, providing secure access control, auditing, alerting, and recording for any privileged account.
BeyondTrust’s focus on identity and access security is pivotal to digital transformation success, ensuring that as organizations evolve, their cybersecurity measures remain robust and effective.
In summary, BeyondTrust’s Privileged Access Management solutions provide organizations with the tools necessary to secure, manage, and audit privileged access, thereby enhancing overall cybersecurity posture.

BeyondTrust’s Privileged Remote Access, PRA, solution offers organizations secure and efficient management of privileged access to critical systems and applications. By enabling secure remote connections, PRA ensures that only authorized users can access sensitive resources, thereby reducing the risk of unauthorized access and potential security breaches.
In 2021, BeyondTrust was recognized as a Leader in the Gartner Magic Quadrant for Privileged Access Management, highlighting its comprehensive and integrated approach to privileged access security.
BeyondTrust continues to enhance its PRA solution, incorporating features like FIDO2/YubiKey support for passwordless authentication and streamlined vendor onboarding via automation. These advancements aim to provide organizations with a more secure and user-friendly experience.
For organizations seeking to bolster their security posture, BeyondTrust’s Privileged Remote Access offers a comprehensive solution to manage and monitor privileged access effectively.

BeyondTrust Secure Remote Support is a comprehensive solution that enables IT teams to provide secure, efficient remote assistance across various platforms, including Windows, Mac, Linux, iOS, Android, and network devices. This tool empowers service desks to manage and view user access privileges through customizable reports, ensuring compliance and enhancing security. It also extends the capabilities of native group policy management tools to include specific settings for Unix, Linux, and Mac systems, achieving consistent configurations across the enterprise. Additionally, BeyondTrust offers enhanced security features such as single sign-on (SSO) for enterprise applications and centralized control over access to non-Windows systems via Active Directory. The solution supports privileged remote access without the need for a VPN,

BeyondTrust’s Endpoint Privileged Management, EPM, is a comprehensive solution designed to secure and manage privileged access across an organization’s endpoints. By enforcing the principle of least privilege, EPM ensures that users operate with standard permissions, elevating privileges only when necessary and under controlled conditions. This approach significantly reduces the risk of insider threats and malware attacks.
A key feature of BeyondTrust’s EPM is its ability to monitor and control privileged access in real-time. This continuous oversight allows IT administrators to detect and respond to potential threats promptly, enhancing the organization’s security posture. Additionally, the solution offers detailed auditing and reporting capabilities, facilitating compliance with industry regulations and internal policies.

BeyondTrust’s Identity Security Insights solution addresses modern challenges by integrating with trusted identity providers and cloud services. It offers real-time threat analysis, providing a unified view of identities, entitlements, and privileged access, while suggesting actionable security enhancements.
The solution also addresses the growing need for secure remote access, offering robust Vendor Privileged Access Management (VPAM) and Cloud Infrastructure Access capabilities. These features enable secure, streamlined access for trusted vendors and empower cloud developers and DevOps teams with seamless yet secure connectivity.
BeyondTrust’s dedication to enhancing identity security is evident through its continuous product enhancements and strategic partnerships, ensuring comprehensive and secure solutions for organizations.

BeyondTrust’s Just-in-Time (JIT) Access, is a pivotal component of Privileged Access Management (PAM) solutions, designed to enhance security by granting privileged access only when necessary and for a limited duration. This approach minimizes the risks associated with standing privileges, which can be exploited by malicious actors.
By implementing JIT Access, organizations can enforce the principle of least privilege, ensuring that users have the minimum level of access required to perform their tasks. This strategy not only reduces the attack surface but also aids in compliance with various regulatory standards.
BeyondTrust’s JIT Access solutions offer features such as automated password management, session monitoring, and detailed auditing. These capabilities provide real-time visibility and control over privileged accounts, enabling organizations to detect and respond to potential threats promptly.
In the context of the European Union’s NIS2 Directive, which aims to enhance cybersecurity across member states, adopting JIT Access solutions like those offered by BeyondTrust is crucial. These solutions help organizations meet the directive’s stringent requirements for securing critical infrastructure and sensitive data.
In summary, BeyondTrust’s Just-in-Time Access is an essential tool for organizations seeking to bolster their cybersecurity posture by ensuring that privileged access is granted only when necessary and for the shortest time possible.

Keeper Password Management is a robust solution designed to enhance cybersecurity by securely storing and managing passwords. It offers features such as strong password generation, secure storage, and monitoring of security policies and practices within an organization. By utilizing Keeper, businesses can defend against cyber threats and ensure the safety of sensitive information.
Additionally, Keeper provides passwordless authentication, allowing organizations to achieve comprehensive security and access control across all applications and websites without requiring end-users to remember passwords.
For those considering the use of passphrases, Keeper offers a passphrase generator to simplify logins. This tool helps users create, store, and manage logins for all their accounts, providing a secure yet easy-to-remember approach to authentication.
In summary, Keeper Password Management is a comprehensive tool that enhances cybersecurity by securely managing passwords, offering passwordless authentication, and simplifying logins through passphrase generation.

Keeper SSO Extender is a powerful tool designed to integrate Single Sign-On (SSO) capabilities into an organization’s existing systems. With this solution, users can access multiple applications using a single set of credentials, reducing the complexity of login processes and improving overall security. By streamlining authentication, the Keeper SSO Extender enhances user experience and minimizes the risk of password-related breaches.
This integration simplifies user management, enabling IT teams to manage access with greater ease and control. The solution is ideal for organizations seeking to improve both security and productivity, aligning with best practices in cybersecurity. By adopting the Keeper SSO Extender, companies can ensure more efficient operations while strengthening their defense against unauthorized access.

In today’s digital age, protecting sensitive data is more crucial than ever. KEEPER Dark Web Monitoring offers a powerful solution to detect and mitigate potential threats hiding in the dark web.
KEEPER Dark Web Monitoring is a service that continuously scans the dark web for exposed information, such as personal credentials, financial details, and proprietary business data. By identifying compromised data early, businesses and individuals can take proactive steps to prevent data breaches and identity theft.
KEEPER uses advanced algorithms to monitor dark web forums, marketplaces, and other hidden platforms. When compromised data related to your organization or personal details is detected, alerts are generated immediately, allowing for swift action.
Benefits of KEEPER Dark Web Monitoring:
- Early Detection: Detect exposed data before it can be exploited by malicious actors.
- Proactive Security: Take preventive measures to avoid potential breaches.
- Comprehensive Coverage: Monitor a wide range of dark web sources for thorough protection.
By integrating KEEPER Dark Web Monitoring into your cybersecurity strategy, you can significantly enhance your defense against emerging threats.

INVICTI is a leading Web Application Security solution that automates the discovery and testing of web applications and APIs. It offers comprehensive coverage, ensuring that all web assets are identified and secured, regardless of the technology or framework used. By integrating dynamic application security testing (DAST) with proof-based scanning, INVICTI provides accurate and actionable results, minimizing false positives and manual verification efforts. This approach enables organizations to detect and resolve vulnerabilities early in the software development lifecycle, enhancing overall security posture.

Invicti is a leading provider of web application and API Security solutions, offering automated and accurate testing to identify and remediate vulnerabilities across thousands of web assets. Their platform integrates seamlessly into the software development lifecycle (SDLC), automating security tasks and saving teams hundreds of hours each month. By combining dynamic application security testing (DAST) with interactive application security testing (IAST), Invicti ensures comprehensive coverage and reduced false positives. This approach allows organizations to proactively secure their applications and APIs, enhancing their overall cybersecurity posture.
Invicti’s API security features include multi-layered API discovery, support for REST, SOAP, and GraphQL APIs, and the ability to import API definitions for thorough testing. Their platform also offers detailed reporting and integration with issue tracking systems, enabling efficient vulnerability management. By leveraging Invicti’s solutions, businesses can effectively protect their web applications and APIs from emerging threats.

Invicti’s Dynamic Application Security Testing, DAST, is a crucial component of modern cybersecurity strategies, focusing on identifying vulnerabilities in running applications and APIs. Unlike Static Application Security Testing (SAST), which examines source code, DAST evaluates applications in their operational environment, providing a real-time, outside-in perspective on security.
DAST tools, such as Invicti’s solutions, simulate attacks to uncover issues like SQL injection, cross-site scripting (XSS), and misconfigurations. This approach ensures comprehensive coverage across the entire potential attack surface, including dynamic content security and API security.
A key advantage of DAST is its ability to integrate seamlessly into the software development lifecycle (SDLC). By automating security testing, organizations can detect and address vulnerabilities early in the development process, reducing the risk of security incidents and enhancing overall application security.
In summary, Invicti’s DAST solutions offer a robust, automated approach to application security, enabling organizations to proactively identify and mitigate vulnerabilities in their web applications and APIs.

Invicti’s Static Application Security Testing, SAST, focuses on finding vulnerabilities in your code early in the development cycle, minimizing risks before software reaches production. By integrating seamlessly into existing workflows, Invicti empowers development teams to catch critical security flaws efficiently. Unlike other solutions, Invicti’s SAST tool provides actionable insights, reducing false positives and enhancing code quality. With a user-friendly interface and robust scalability, Invicti’s SAST is trusted by enterprises to secure web applications and APIs at scale.

Kaseya’s Remote Monitoring and Management, RMM, solutions, such as Datto RMM and Kaseya VSA, offer comprehensive tools for IT professionals to oversee and maintain endpoints, networks, and cloud services. These platforms provide real-time monitoring, advanced automation, and rapid troubleshooting capabilities, enabling proactive issue resolution and minimizing downtime. With intuitive dashboards and detailed reporting, IT teams gain clear insights into their IT landscape, enhancing operational efficiency and security.
Key Features:
- Advanced Software Management: Streamline software deployment and updates across all devices.
- Flexible Patch Management: Automate the application of patches to ensure systems are up-to-date and secure.
- Monitoring Automation and Scripting: Set up automated monitoring and scripts to handle routine tasks efficiently.
- Rapid Remote Access and Support: Quickly access and resolve issues on remote devices.
- Auto-Remediation of Issues: Automatically address common problems without manual intervention.
- Asset and Inventory Management: Keep track of all hardware and software assets within the network.
- Reporting and Analysis: Generate detailed reports to analyze performance and identify areas for improvement.
- IT Automation: Implement automated workflows to reduce manual tasks and increase efficiency.
By integrating these features, Kaseya’s RMM solutions empower IT professionals to deliver services more efficiently, securely, and cost-effectively.

Kaseya Unified Backup is a comprehensive solution designed to streamline IT management by integrating endpoint management, security, backup, and automation into a single platform. This unified approach enables IT professionals to efficiently oversee and protect their infrastructure, ensuring data integrity and system reliability.
Key Features:
- Endpoint Management: Advanced remote monitoring and maintenance tools provide complete control over endpoints, networks, and cloud services. Real-time monitoring, automation, and quick troubleshooting help resolve issues proactively.
- Security: Integrated security features, including endpoint detection and response (EDR), antivirus protection, and ransomware detection, offer robust defense against cyber threats. These tools ensure compliance with industry standards and protect critical data.
- Backup: Reliable endpoint backup solutions safeguard data integrity with automated processes and incremental backups. Encryption and compliance features maintain data security and regulatory alignment.
- Automation: Built-in automation streamlines workflows, reduces manual errors, and simplifies complex tasks, enhancing overall efficiency.
By consolidating these essential IT functions, Kaseya Unified Backup provides a cost-effective and efficient solution for managing, securing, backing up, and automating endpoints. This integration simplifies operations, boosts security, and improves service delivery for IT professionals.

Kaseya’s Professional Service Automation, PSA, is a comprehensive, automated, and cost-effective platform trusted by over 500,000 IT professionals worldwide to manage and secure more than 300 million devices.
This AI-powered solution streamlines IT management, security, and backup processes, enabling Managed Service Providers (MSPs) and IT departments to enhance efficiency and profitability. Kaseya’s open platform and customer-centric approach deliver the technology SMBs and MSPs need to reach new heights of success.
By consolidating essential IT functions into a single interface, Kaseya 365 offers a seamless way to manage, secure, back up, and automate endpoints under one affordable subscription. This integration simplifies operations, reduces costs, and improves service delivery for IT professionals.
In summary, Kaseya’s PSA provides a robust, all-in-one solution for IT management, empowering organizations to effectively oversee and protect their IT infrastructure.

Vonahi, a cybersecurity firm specializing in Automated Penetration Testing solutions, has introduced a new prospecting test feature. This tool enables Managed Service Providers (MSPs) to offer potential clients preliminary pentest evaluations, demonstrating immediate value and facilitating the acquisition of new business.
Additionally, Vonahi has enhanced its reporting capabilities by allowing custom-branded reports to be exported to Microsoft Word. This feature enables MSPs to add additional data and customize report themes to align with their company branding, providing a more personalized experience for clients.
These developments reflect Vonahi’s commitment to empowering MSPs with advanced tools that streamline the penetration testing process and improve client engagement. By offering customizable and client-focused solutions, Vonahi continues to support MSPs in delivering high-quality cybersecurity services.

Kaseya’s IT Complete platform offers a comprehensive suite of tools for IT management, security, backup, and automation. This unified approach streamlines operations, enhances security, and reduces costs for IT departments and managed service providers (MSPs).
Key Features:
- Manage: Advanced remote monitoring and management solutions, including Datto RMM and Kaseya VSA, provide real-time oversight of endpoints, networks, and cloud services. These tools enable proactive issue resolution and efficient IT operations.
- Secure: Integrated security features such as endpoint detection and response (EDR), antivirus protection, and ransomware detection safeguard against evolving cyber threats. These measures ensure data integrity and compliance with industry standards.
- Backup: Reliable endpoint backup solutions with automated processes and end-to-end encryption protect critical data, ensuring quick recovery in case of data loss or system failure.
- Automate: Built-in automation tools streamline repetitive tasks, boost productivity, and reduce manual errors, allowing IT teams to focus on strategic initiatives.
By consolidating these essential IT functions into a single platform, Kaseya IT Complete empowers organizations to manage their IT environments more effectively and securely.

Peplink WAN Bonding is a technology that combines multiple internet connections into a single, more reliable and high-speed link. By utilizing Peplink’s SpeedFusion technology, businesses can achieve seamless failover, enhanced bandwidth, and improved network resilience.
This solution is ideal for enterprises, remote workers, and mobile deployments that require uninterrupted internet connectivity. It aggregates different WAN sources, such as fiber, DSL, 4G, and Starlink, ensuring maximum uptime and optimal performance.
Peplink’s WAN Bonding is widely used in sectors like maritime, transportation, and enterprise networking. It enhances VoIP, video conferencing, and cloud applications by reducing latency and jitter. The technology also provides strong security features, including VPN encryption, ensuring safe data transmission.
NSS offers Peplink solutions in Greece, enabling businesses to benefit from cutting-edge connectivity and network optimization.

Peplink VPN Bonding, powered by SpeedFusion, is a cutting-edge technology that aggregates multiple internet connections—such as DSL, fiber, 4G/5G, and satellite—into a single, high-performance, and highly reliable VPN tunnel. This ensures seamless connectivity with increased bandwidth, lower latency, and automatic failover.
Unlike traditional VPNs that rely on a single connection, Peplink’s SpeedFusion technology combines multiple WAN links, distributing data across them for optimal performance. This is ideal for businesses with remote offices, mobile applications, and industries requiring uninterrupted communication, such as maritime, transportation, and emergency services.
With features like Hot Failover, WAN Smoothing, and Bandwidth Bonding, Peplink ensures continuous uptime and superior quality of service. It is widely used in industries requiring high availability, secure remote access, and optimized network performance.

SealPath is a robust Information Rights Management (IRM) solution that empowers organizations to protect and control their critical documents, regardless of their location. By leveraging Microsoft Rights Management Services (AD-RMS), SealPath ensures seamless integration with Microsoft Office applications, allowing users to access protected documents without additional software installations.
With SealPath, companies can define granular protection policies, automate document protection, and monitor access in real-time. This capability is particularly beneficial for industries such as legal, biotechnology, and finance, where secure document sharing is paramount.
In summary, SealPath provides a comprehensive solution for document security, ensuring that organizations can share information securely while retaining full control over their critical assets.

SealPath is a Document Security solution that offers real-time control over document permissions, even after sharing. It is available in both Cloud-SaaS mode for quick deployment and on-premise for companies requiring full control over their infrastructure. SealPath protects documents wherever they are, allowing convenient and secure sharing. It limits actions such as reading, printing, sharing, and copying, ensuring only authorized users can access the information.
The solution also monitors document access, providing notifications when recipients view the document, and offers detailed auditing capabilities. SealPath does not store your documents, giving you the freedom to choose where to save them. It utilizes Microsoft AD RMS technology, a proven information protection technology that integrates with Microsoft Office and other Microsoft products.
SealPath is designed for teams and companies that require flexible, simple, and secure document exchange, benefiting industries such as legal, industrial design, biotechnology, research, and finance. It helps protect critical information, share documents securely, prevent data loss, comply with data protection audits, and integrate seamlessly with existing workflows.

ARRAY WAF is a robust Web Application Firewall (WAF) solution designed to protect web applications from a wide range of cyber threats, including SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities. By analyzing incoming traffic, ARRAY WAF identifies and blocks malicious requests, ensuring that only legitimate users can access your web applications.
NSS, a leading provider of cybersecurity solutions, offers ARRAY WAF as part of its comprehensive suite of services. Their expertise in IT and security management ensures that clients receive top-tier protection tailored to their specific needs. By integrating ARRAY WAF, organizations can enhance their security posture, safeguard sensitive data, and maintain the integrity of their web applications.

ARRAY Enterprise SSL VPN is a powerful solution designed to provide secure remote access for enterprises. It offers scalability, reliability, flexibility, and robust security to meet the demands of modern businesses.
The AG Series VPN gateways from Array Networks deliver high-performance secure remote access, ensuring that employees, partners, and customers can connect to corporate resources safely from any location. These gateways support multi-factor authentication, endpoint security compliance, and granular access controls, making them a preferred choice for organizations that require a high level of security.
With a focus on seamless connectivity, ARRAY SSL VPN enhances user experience by offering features such as single sign-on (SSO), dynamic access policies, and integration with existing security infrastructure. Whether deployed on-premises or in the cloud, it provides a comprehensive solution for organizations looking to enable secure remote work.

AArray Networks is a leading provider of Application Delivery solutions, specializing in secure and efficient management of application traffic. Their products, such as the APV Series Application Delivery Controllers, offer advanced features like SSL acceleration, load balancing, and traffic management across layers 2-7. These solutions are designed to enhance application performance, security, and availability for enterprise data centers and websites.
Array Networks’ commitment to innovation and customer satisfaction has solidified its position as a trusted provider of application delivery solutions worldwide.

Array Networks offers robust DDoS Protection solutions through its ASF Series Application Security Firewalls and APV Series Application Delivery Controllers. These products provide comprehensive defense against Layer 3 to Layer 7 DDoS attacks, ensuring the availability and security of web applications.
Key Features:
- Advanced DDoS Mitigation: The ASF Series employs both negative and positive security models to detect and mitigate a wide range of DDoS attacks, including HTTP floods, SSL handshake attacks, and more.
- Web Application Firewall (WAF): Integrated WAF capabilities protect against common web vulnerabilities such as SQL injection, cross-site scripting (XSS), and cookie/session hijacking.
- SSL Offloading: The APV Series offers SSL offloading to reduce the processing burden on backend servers, enhancing performance and enabling deep inspection of encrypted traffic.
- Machine Learning Integration: Array’s DDoS protection features machine learning for anomaly detection and automatic configuration of threshold values, improving the accuracy and responsiveness of threat mitigation.
By leveraging these solutions, organizations can effectively safeguard their applications against evolving DDoS threats, ensuring uninterrupted service and data integrity.

ARRAY Server Load Balancing solutions, offered by NSS, are designed to enhance the performance, availability, and scalability of applications and services. By efficiently distributing incoming traffic across multiple servers, these solutions ensure high availability and minimal downtime. This approach is particularly beneficial for industries and enterprises aiming to optimize business operations.
A notable example of this technology in action is eClinicalWorks’ partnership with Array Networks. This collaboration enabled eClinicalWorks to achieve greater scalability in their data centers, effectively managing increased web and application traffic. The load balancing feature played a crucial role in distributing traffic efficiently, resulting in reduced downtime and improved service reliability.
Additionally, Array Networks has introduced a new version of its Application Delivery Controller, specifically designed to address the scalability needs of cloud computing environments. This version offers significant improvements in server offload and acceleration capabilities, enhancing overall application performance.
In summary, ARRAY Server Load Balancing solutions provide robust and scalable options for businesses seeking to optimize their application delivery and performance.

Array Networks is a leading provider of application delivery networking solutions, specializing in enhancing Network Visibility and performance. Their products, such as the Application Delivery Controllers (ADCs) and the AVX Series Network Functions Platform, offer comprehensive monitoring and management capabilities. These solutions ensure optimal application performance, security, and user experience by providing deep insights into traffic patterns and user behavior.
A key feature of Array Networks’ offerings is the SSL Intercept solution, which decrypts SSL traffic to allow inspection and remediation by virtualized security functions. This capability enables organizations to detect and mitigate threats hidden within encrypted traffic, thereby enhancing overall network security.
Additionally, the Array Management Platform (AMP) provides centralized monitoring and management of Array Networks’ appliances, simplifying administration and improving operational efficiency. AMP’s intuitive dashboard and analysis capabilities enable administrators to quickly identify and address performance and security issues.
By leveraging these solutions, organizations can achieve enhanced network visibility, leading to improved application performance, increased security, and greater operational efficiency.
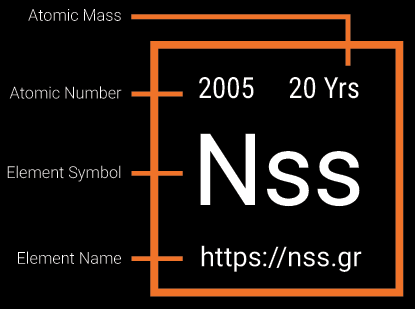

NSS started in 2005 in a basement with only 3 employees. Over time, it moved to a new office in 2007, focusing on distribution by 2008. Key milestones include becoming a Sophos distributor in SE Europe in 2011, becoming a multi-vendor training center in SE Europe by 2015, opening the MSP Excellence Center in 2017, initializing the PAM Excellence center in 2020, the Offensive Security Excellence Center in 2023, and expanding its expertise with services in cybersecurity, identity security, and vulnerability assessments. It now operates across 13 countries and supports over 3,500 customers.
NSS collaborates with a diverse range of leading IT vendors to provide comprehensive solutions to its clients. International vendors like Sophos, Fortra, BeyondTrust, Kaseya, Keeper, Datto, Invicti, Peplink, Sealpath, Array, Mailstore, Acunetix, Exagrid, SEP, GlobalSign, MailSpec, Logpoint to mention a few.
NSS is revolutionizing the distribution of cutting-edge technology solutions by offering innovative, affordable, and high-quality products to Managed Service Providers (MSPs). As a value-added distributor, NSS focuses on cybersecurity, services automation, cloud transformation, IT security, and infrastructure management. By collaborating with top vendors, NSS ensures its clients access to the most advanced and reliable solutions available. Through its commitment to providing expert training and customer support, NSS empowers MSPs to enhance their service offerings and stay ahead in an increasingly competitive market.
In the evolving world of technology, NSS is reshaping the distribution model by blending value, quality, and expertise. Its extensive portfolio covers areas such as data security, privileged access management, and threat resilience. The company focuses on simplifying complex technologies, making them accessible to a wider range of businesses, from SMBs to large enterprises. By emphasizing GDPR, NIS2 and DORA compliance, NSS ensures that its solutions meet the highest regulations and standards of privacy and security.
NSS’s dedication to customer success is a cornerstone of its operations. The company’s comprehensive support system goes beyond product delivery; it includes hands-on training, technical assistance, and strategic advice. This hands-on approach not only helps customers implement solutions effectively but also ensures that they can maximize their investment in cutting-edge technology.
With a forward-thinking approach to technology distribution, NSS stands out as a leader in the industry. By offering affordable yet highly advanced solutions, NSS is empowering businesses to embrace digital transformation with confidence. Whether you are a small business looking for scalable cloud solutions or an enterprise seeking robust security systems, NSS has the expertise and products to meet your needs.














