True Privilege™ is BeyondTrust’s industry leading capability for providing a complete view of all the privileges an identity has access to, including both intended and unintended privileges. Made visible by the True Privilege Graph feature in Identity Security Insights™, it goes beyond traditional views of privileges directly assigned to encompass hidden misconfigurations that attackers can exploit to elevate privileges further.
Seeing the True Privilege of an identity means having the ability to understand where privilege and risk truly exist. It’s all about seeing this bigger picture.
In recent years organizations have experienced exponential growth in the number of identities (human, machine, and agentic AI) and the accounts, privileges, and entitlements they can access across cloud, SaaS, and hybrid environments. To secure these identities effectively, you need to be able to cross silos and understand all the Paths to Privilege™ that exist and the True Privilege that this represents.
From Least Privilege to True Privilege: Why Modern Identity Security Demands a New Approach
Privileged Access Management (PAM) is a cornerstone in identity security, designed to reduce risk by enforcing the principle of least privilege. However, in modern environments, a major challenge is that PAM is often thought about in silos. For example, one might focus only on managing highly privileged Windows Domain Administrator accounts with little regard for the plethora of privileged cloud and SaaS roles.
To effectively protect our organizations from modern identity threats, we need consider the bigger picture and understand all the escalation paths across the entire identity attack surface. This is precisely what threat actors do, which is why 90% of organizations experienced an identity-related breach in the past year.
How True Privilege Protects Against Modern Attacks
Meet Amy: a real-world example of hidden risk.
Let’s consider Amy, a developer whose identity has multiple accounts and access to different systems.

Amy has various privileges directly assigned to her accounts, which traditional solutions might have visibility into—but often in a disconnected way. This means one tool might see her AWS privileges, while another sees her Active Directory privileges, making it difficult to get a complete picture of her assigned privilege and access.
But the real risk lies in the indirect or unintended privilege pathways. These can arise from misconfigurations, inherited rights, or hidden connections within the identity infrastructure. In Amy’s case, several apps she manages in Azure have service principals with the ability to assign the Global Administrator role. This means that even though Amy isn’t a Global Administrator herself, a path exists for her to gain that highly privileged role, either for herself or someone else.
Putting True Privilege into Practice
This is all about asking the right questions. Do you know who are the most privileged identities in your organization? How can you be sure a simple misconfiguration won’t allow any user to become a domain administrator? And how do you ensure proper controls, like multi-factor authentication (MFA), are in place for these privileged identities?
For most organizations, these questions are at best difficult but more likely next-to-impossible to answer with existing tools.
BeyondTrust Pathfinder the Platform with True Privilege Graph
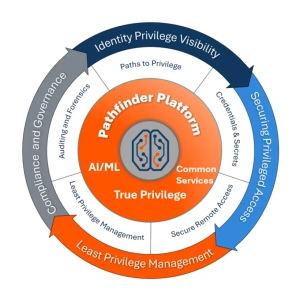
These fundamental identity security questions around sprawling privileges, escalation paths, and solution silos are why we launched our BeyondTrust Pathfinder Platform, a unified and cohesive console. Pathfinder provides organizations with adaptive, intelligent, and risk-aware identity security.
Its deep, cross-domain intelligence capabilities, powered by Identity Security Insights, integrate with your existing solutions to offer context-rich visibility into every identity, going far beyond what traditional tools can offer.
Using AI models, BeyondTrust dynamically maps the True Privilege of identities across all systems and continuously uncovers new Paths to Privilege as your environment changes.
This pragmatic, AI-powered approach provides a level of visibility that previously required a dedicated team of identity security specialists. With Pathfinder, you can remediate risks and reduce your identity attack surface before attackers can exploit them.
Seeing and Addressing True Privilege™, and the Future of PAM
The Modern, Holistic Approach to Identity Security You Need
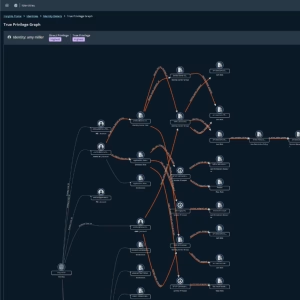
 No one likes scrolling through endless lists to find an answer. The BeyondTrust True Privilege graph allows you to visually explore the Paths to Privilege for any identity. This makes it easy to see assigned privileges and proactively uncover and fix escalation paths before a threat actor exploits them.
No one likes scrolling through endless lists to find an answer. The BeyondTrust True Privilege graph allows you to visually explore the Paths to Privilege for any identity. This makes it easy to see assigned privileges and proactively uncover and fix escalation paths before a threat actor exploits them.
Pathfinder offers the full suite of BeyondTrust capabilities, allowing you to easily manage privileges and access on-premises, in the cloud, or in OT environments. Whether you want to remove local admin rights, reduce standing privileges with just-in-time (JIT) access, or provide secure remote access without a VPN, Pathfinder is here to help you see, manage, and protect all your Paths to Privilege.
To see the True Privileges in your environment, start our free Identity Security Risk Assessment today.
Source: BeyondTrust





