NIS2, the reformed edition of the 2016 Network and Information Security (NIS) directive, was entered into force at the start of 2023, following multi-year European Parliament negotiations. Member states have until 17th October 2024 to adopt and publish measures complying with NIS2.
With a little less than a year left for affected organizations to comply with the new requirements, we sat down with Lee Elliott, Director of Solutions Engineering at BeyondTrust, to learn more about NIS2 and its impact on national security. This blog will provide answers to the leading questions about NIS2 to help you prepare your organization to meet the coming deadline.
Q1: What is NIS2?
The Network and Information Security 2 (NIS2) Directive is a landmark piece of European cybersecurity legislation that provides legal measures to boost the overall level of cybersecurity in the European Union (EU). It does so by setting a common, high standard for companies and organizations to comply with in terms of their cybersecurity posture and obligations.
Q2: Who does NIS2 apply to?
Businesses identified by the Member States as operators of “important” or “essential” services. Most of the organisations held accountable by NIS2 are Critical National Infrastructure (CNI) and run Operational Technology (OT) and industrial systems networks.
NIS2 regulations not only cover important or essential services, but also any breach in their supply chain. This means that their subcontractors and suppliers, wherever they are based, need to be as secure as the NIS2 requirements.
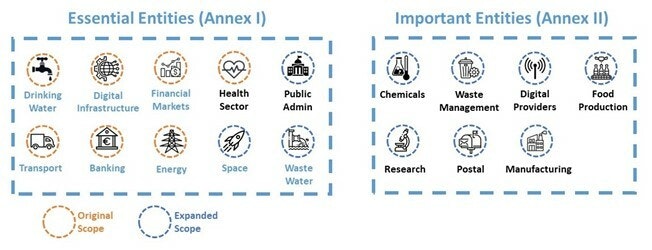
Q3: NIS vs NIS2 – What’s the difference?
NIS2 introduces updates to the EU cybersecurity rules that were originally introduced in 2016 in order to modernise the existing legal framework and keep up with increased digitisation and an evolving cybersecurity threat landscape.
Some key differences include:
- More industry sectors included – the scope of cybersecurity rules has expanded to new sectors and entities, particularly incorporating manufacturing and other OT industries. Company criticality and size is also taken into account.
- New incident response and crisis management reporting requirements – NIS2 requires improvement of the incident response capacities, including strengthened incident reporting obligations, more precise reporting processes, and timeline provisions.
- Enhanced security requirements and controls – Security requirements are strengthened, with focused vulnerability handling and disclosure, policies and procedures to assess the effectiveness of cybersecurity risk management measures, basic computer hygiene practices and cybersecurity training, the effective use of cryptography, human resources security, access control policies, and asset management.
- Bigger penalties – NIS2 introduces more severe penalties for compliance failures. Administrative fines vary based on entity status:
- Essential entity fines can be up to €10,000,000 or 2% of the total annual worldwide turnover in the previous fiscal year (whichever is higher);
- Important entity fines can be as much as €7,000,000 or 1.4% of the total annual worldwide turnover in the previous fiscal year of the company (whichever is higher).
- Increased liability – C-level executives who are responsible for the Risk and Governance of their infrastructure will be held personally liable for a breach and could be removed from their post.
Q4: When does NIS2 come into effect?
The deadline for Member States to transpose the NIS2 Directive into applicable, national law is 17 October 2024. Companies need to be fully compliant with the directive’s updated requirements before this date or they may face severe consequences, including financial penalties and damage to reputation.
Q5: Why is there a focus on operational technology (OT) within NIS2?
OT security has become much more critical because of the recent spate of high-profile attacks. It has also become the focus of increasing compliance frameworks. In terms of security, OT is playing catchup with IT. In IT networks, most security fundamentals have been put in place, but in OT, controls like change management, access control, and vulnerability management are still not being applied.
Q6: What are the challenges of managing and securing OT Environments?
I think it boils down to the focus of an OT environment. For the most part, these environments are manufacturing plants—factories that are producing an output. Availability is paramount. Any downtime will cost a measurable amount based on loss of output. Of course, with CNI, availability becomes even more important as any downtime may have a detrimental effect on the nation! And if you think that IT is more data-centric and so integrity is more of a focus, remember: you can back up data, but it’s not so easy to do with the flow of gas or oil!
Also, OT environments are full of legacy, and sometimes unsupported, equipment. Refresh cycles could be in the decades rather than the 3-to-6-year range that is typically seen in IT. There is an element of technical debt with systems that were never designed to operate with new cyberthreats in mind.
Lastly, there is a temptation for companies to use the authentication and security services they have in IT for their OT environment. For example, using the corporate Active Directory to manage the account authentication and authorisation for OT users. This is a really bad idea. The two areas should be segmented to prevent a breach from crossing from one environment to the other, resulting in a much larger impact.
Q7: What are the next steps for organizations? Should they start mapping NIS2 to more familiar frameworks? What will a gap analysis likely show against the new regulations?
This really depends on the Governance, Risk & Compliance (GRC) team within the company. They should be able to digest the new requirements and see where their existing controls are sufficient and where there are gaps. You must consider also that independent auditors will ensure that all controls are in place and satisfy the requirements. If not, they will enforce plans and penalty-driven timelines to ensure compliance.
To assist with this, NIS2 encourages “the use of European and international standards and technical specifications relevant to the security of network and information systems”, for example ISO27001.
The basics (endpoint security, EDR, antivirus etc.) should already have been covered for NIS or other required security frameworks, but the biggest gap is still phishing. Enforcing least privilege and better identity management will be a key area of focus for most organizations.
Q8: If least privilege is the answer, why has it not been adopted more widely?
Least privilege has been around for a long time. The problem people find is that it’s easy to say, but difficult to do—especially on endpoints, servers, and desktops—because people sometimes do need a certain amount of privilege to do their job. By taking that away, you’re preventing them from actually being productive.
When companies are measured in response times, SLAs, and how quickly get things fixed, and when having applications go down can cost the company millions per day, security sometimes takes a backseat. Then it’s only when they’ve had a breach, or when they think they’re going to have a breach, that they start thinking about it. So, least privilege is difficult from that standpoint. It should be as simple as having the tools in place that allow people to still do their work, with policies that allow them to do what they need to do, but securely.
Q9: What are the specific challenges of incorporating third parties into your security strategy?
Third parties can be seen as the weakest link in the cyber defence chain. Every company relies on third parties to support their Tier 1 business services, but the security of the company as a whole is only as good as the security of the worst third-party company.
This threat is old: one of the first documented cyberattacks occurred on the US hypermarket, Target, in 2013. The attack was caused by a breached third party when the heating and air conditioning support company Target used was breached. The company had VPN access into Target’s stores to monitor and patch the air conditioning systems, but during the recon phase, the threat actors also gained access to Point-of-Sale registers. They installed credit card skimming software and stole credit card details from approximately 40 million customers, eventually costing Target USD420 million.
With the updates in NIS2, incorporating third parties into your security strategy is now paramount. Companies must impose a minimal cybersecurity maturity level on their suppliers and will be responsible for assessing that supplier, not the National Authorities.
Q10: How does technology add to the vendor privileged access management (VPAM) challenge?
Controlling third party access to internal systems is a critical function of supply chain security. However, current technology used by many companies for providing remote access is outdated and doesn’t provide the necessary controls for giving third parties access securely.
VPNs are susceptible to vulnerabilities – just search any CVE database to see. Travelex forgot to patch its VPN in 2020 and was hacked via CVE -2019-11510. The attack cost the company $2.3 million in ransom paid to the hackers, and eventually the company was forced into administration.
As another example of where VPAM is needed, in February of 2022, Toyota shut down 14 manufacturing plants at a cost of about $375 million because of a cyberattack on Kojima Industries, a key supplier. Kojima Industries is a small company and is little-known outside Japan, where it produces cup holders, USB sockets, and door pockets for car interiors. However, its modest role in the automotive supply chain is a critical one, and when the company was hacked, it brought Toyota’s entire production line to a stop. Even after the initial crisis was over, it took months for Kojima to get operations back to normal.
Q11: What’s the best solution for managing vendors and third-party users?
Managing third-party vendors is a combination of policy, process, and technology. Providing any one without the others is pointless.
Managing vendor users is always a difficult problem. Where do you create their accounts? How do you know if someone who left has passed their credentials off to their replacement, or even to several people who are now accessing your infrastructure? Modern solutions allow vendors to manage their own remote access account with the necessary controls in place.
Modern administrative and third-party vendor access solutions should provide clientless access with flexible authentication methods, approval workflows, just-in-time access windows, and visibility and auditing. The latter is important not only for security, but also to ensure vendors are adhering to the agreed contract and process. Additionally, integrating with change procedures and using the change number as an additional verification would be useful.
Q12: There is an argument for accepting legal risk when the cost of compliance exceeds the cost of the fines—why should people spend money on NIS2 compliance instead of just accepting the gaps?
Optimism bias is a tendency to overestimate the likelihood that good things will happen to us while underestimating the probability that negative events will impact our lives. This can affect businesses when company leaders believe they will never be targeted by threat actors.
Mitigating a risk to a lower level of risk so that it can be accepted is good risk management—as long as the mitigation isn’t a temporary fix. But this is an old argument that predates some of the significant attacks on OT/IT environments, and regulatory fines are only part of the cost.
For example, the 2021 Colonial Pipeline ransomware attack cost the company $4.4 billion to pay the threat actors, Darkside. But it also caused a six-day shutdown of fuel supply, which affected airports and fuel stations to such a degree that a State of Emergency was declared. The interesting fact about this attack is that it didn’t directly affect the OT equipment. It shut down the billing infrastructure of the company, but because the extent of the breach was unknown, production was shut down as a precaution.
While this attack is undeniably focused on the US, it serves as an illustration that a breach can result in financial expenses in paying hackers. Moreover, the reputational harm inflicted on both the company and individuals involved can be equally expensive. If this had happened in the EU, there would have been the additional expense of the fines imposed by NIS2.
In addition to financial and reputational risks, under NIS2, individual C-Level executives responsible for the Risk and Governance of their infrastructure face accountability and potential removal from their positions—a risk they might not be willing to accept.
Next steps: achieve NIS2 compliance and secure your identity perimeter with BeyondTrust
BeyondTrust’s innovative solutions are tailored specifically to meet the challenges of securing OT environments and to help organizations secure their identity perimeters. Contact us today to learn more from an expert, and click here to download our whitepaper on how to address the NIS2 directive with Privileged Access Management.
Source: BeyondTrust






