It is with pride and great pleasure that we have the opportunity today to launch our Threat Intelligence application!
With this application, we provide a simple and efficient module for providing contextual attack information to observations from sensor data in your network.
Context
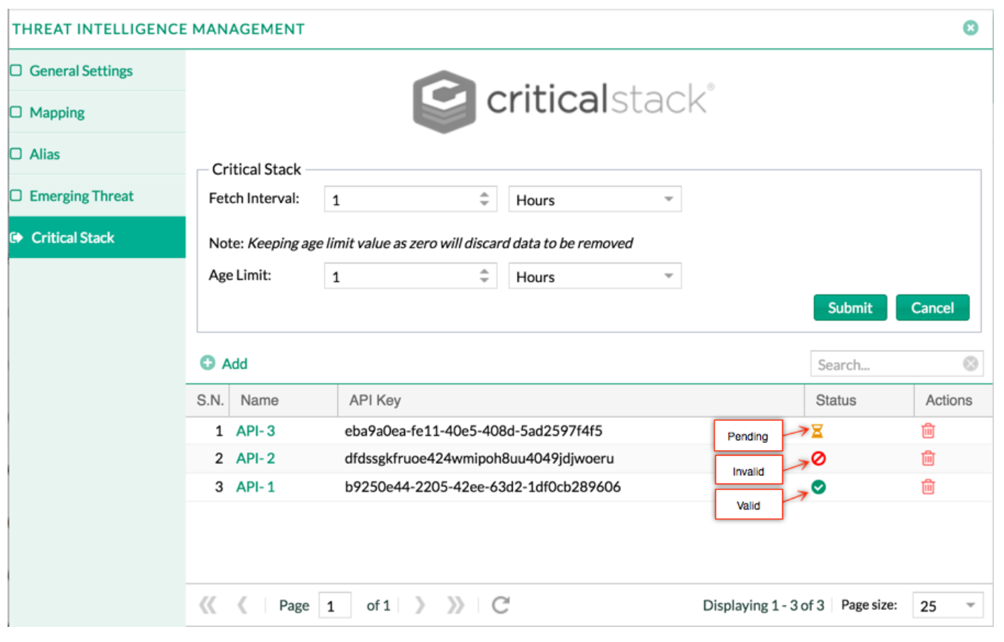
The Threat Intelligence application sources data from best-in-class ProofPoint and the large collection of indicators from Critical Stack. With these sources ingested, LogPoint can analyse structured and unstructed data, alerting if any match between the known-bad indicators and collected enterprise data is identified.
The LogPoint taxonomy and technology stack allows for inspecting any type of collected data, regardless if it comes from your ERP platform, online collaboration platform, hosted Office365 or firewall/antivirus platform. If the data is in LogPoint – it can be correlated with the indicators of compromise.
Reduce Time to Detection
Enterprise log-data is valuable when analysed in and of itself. By correlating your internal data with indicators of compromise, seemingly innocent data can hint at a potential issue. With pre-canned analytics in the form of alert-rules, dashboards and data mappings running out of the box, the Threat Intelligence application is a turn-key application.
Want to Know More?
You can read more about how to get started and set up Threat Intelligence in this blog post.
We also suggest you sign up for our webinar on Threat Intelligence! It takes place December 1st, 2016. Read more about it here.
You can read the original article, here.